gate operator
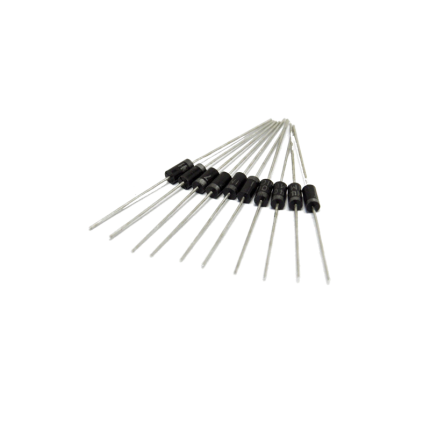
Diode 1N4007
Ship or pick up from our office.
Diode 1N4007
The 1N4007 is a very common and versatile silicon rectifier diode. It's part of the 1N400x series of general-purpose diodes, with the "7" indicating its specific voltage rating. Key Characteristics- Rectifier Diode: Its primary function is to convert alternating current (AC) into pulsating direct current (DC) by allowing current to flow in only one direction.
- High Reverse Voltage Rating: The 1N4007 can withstand a peak repetitive reverse voltage () of 1000V. This makes it suitable for high-voltage applications.
- Average Forward Current: It can handle an average forward current () of 1 Ampere (1A).
- Forward Voltage Drop: When conducting in the forward direction, it has a relatively low forward voltage drop () of approximately 0.7V to 1.1V. This voltage drop represents the power lost within the diode.
- Surge Current Capability: It can handle a non-repetitive peak surge current () of up to 30A for short durations, which is useful for handling initial power-on surges.
- Package Type: It typically comes in a DO-41 axial-lead package, which is a small, cylindrical plastic package with leads on both ends.
- Operating Temperature Range: It operates reliably over a wide temperature range, typically from -55°C to +175°C.
- Forward Bias: When a positive voltage is applied to the anode (P-side) and a negative voltage to the cathode (N-side), the diode is forward-biased. If the applied voltage exceeds the forward voltage drop (around 0.7V for silicon diodes), the diode conducts, allowing current to flow from anode to cathode.
- Reverse Bias: When a negative voltage is applied to the anode and a positive voltage to the cathode, the diode is reverse-biased. In this state, the diode acts like an open switch, blocking current flow. The 1N4007 is designed to withstand up to 1000V in this reverse-biased state before breaking down.
- Rectifier Circuits:
- Half-wave and Full-wave Rectifiers: Essential for converting AC power from the mains (like in household appliances) to DC power for electronic devices.
- Bridge Rectifiers: Used to convert the entire AC waveform into pulsating DC, achieving more efficient rectification.
- Power Supplies: Used for rectifying the AC input in power supply units to provide DC voltage to various components.
- Voltage Protection:
- Reverse Polarity Protection: Prevents damage to circuits if the power supply is connected with incorrect polarity.
- Freewheeling Diodes (Flyback Diodes): Protect sensitive components from voltage spikes generated by inductive loads (like relays, motors, and solenoids) when their magnetic field collapses.
- Voltage Spike Suppression: Helps to suppress transient voltage spikes that can occur due to switching events or lightning, safeguarding delicate electronics.
- Inverters and Converters: Used in various power conversion circuits.
- Current Flow Regulation: Can be used in simple current limiting or flow control applications.
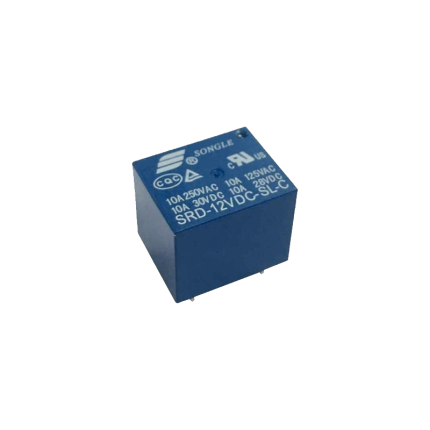
Relay Mini PCB 5-Pin 10A
Ship or pick up from our office.
Relay Mini PCB 5-Pin 10A
A Relay Mini PCB 5-Pin 10A is a compact, electromechanical switch designed to be mounted directly onto a printed circuit board (PCB). It uses a small control voltage to switch a larger current, making it useful for isolating control circuits from power circuits or for switching higher-power loads with a low-power signal. Key Features and Specifications- Mini: This indicates its small physical size, making it suitable for applications where space is limited.
- PCB: This means it's designed for Printed Circuit Board mounting. Its pins are typically configured to be soldered directly into holes on the PCB.
- 5-Pin: These five pins usually consist of:
- Two pins for the coil: These are where the control voltage is applied to energize the coil and activate the relay.
- Three pins for the contacts: These typically include a common (COM) pin, a normally open (NO) pin, and a normally closed (NC) pin.
- 10A: This is the maximum current rating that the relay's contacts can safely switch. It means the relay is capable of handling up to 10 amperes of current through its switched contacts.
- Normally Open (NO): The contact is open when the coil is de-energized and closes when the coil is energized.
- Normally Closed (NC): The contact is closed when the coil is de-energized and opens when the coil is energized.
- Automotive applications: For controlling lights, motors, and other accessories.
- Home automation: Switching lights, appliances, and HVAC systems.
- Industrial control: In PLCs (Programmable Logic Controllers) and other control panels.
- Appliance control: In washing machines, refrigerators, and microwave ovens.
- DIY electronics projects: Where low-power signals need to control higher-power devices.
RFID Tag Access Control
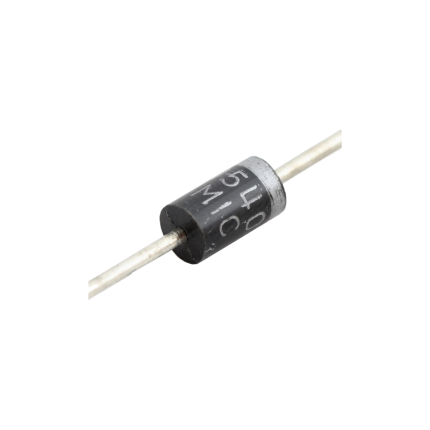
Diode 1N5408
Ship or pick up from our office.
Diode 1N5408
The 1N5408 is a common general-purpose rectifier diode. It's designed to allow electric current to flow primarily in one direction, making it crucial for converting alternating current (AC) to direct current (DC). Think of it like a one-way valve for electricity. It belongs to the 1N540x series of power diodes, known for their ability to handle relatively high current and voltage. Here are its key characteristics and common uses: Key Features- High Reverse Voltage Rating: It can withstand a maximum repetitive reverse voltage () of 1000V. This means it can block high voltages when current tries to flow in the "wrong" direction.
- High Forward Current Capacity: It's rated for an average rectified forward current () of 3 Amperes (A). This indicates it can handle a significant amount of current flowing through it in the correct direction.
- High Surge Current Capability: The 1N5408 can handle non-repetitive peak forward surge currents () of up to 200A for short durations, protecting circuits from sudden power spikes.
- Low Forward Voltage Drop: When conducting, it has a relatively low forward voltage drop () of approximately 1.0V to 1.2V at its rated current. A lower voltage drop means less power is lost as heat.
- Standard Recovery: It's a "standard recovery" diode, meaning its switching speed is relatively slow compared to fast recovery diodes. This makes it suitable for power rectification at lower frequencies (like 50/60 Hz AC).
- DO-201 Package: It typically comes in a DO-201 axial-leaded package, which is a through-hole component with leads extending from both ends, allowing for easy mounting on circuit boards.
- Wide Operating Temperature Range: It can operate and be stored in a wide temperature range, typically from -65°C to +175°C.
- Power Supplies and Rectifiers: This is its primary application. It efficiently converts AC input voltage into pulsating DC, which can then be smoothed by capacitors to provide a stable DC output for electronic devices. This includes full-wave and half-wave rectifier circuits.
- Battery Chargers: Used to convert AC wall power into DC for charging batteries.
- Voltage Regulation Circuits: Helps in maintaining a stable output voltage by rectifying current.
- Protection Circuits: Its ability to block reverse current makes it useful for reverse polarity protection, preventing damage to sensitive components if the power supply is connected incorrectly.
- Freewheeling Diode: Used in inductive circuits (like those with relays or motors) to provide a path for stored energy to dissipate when the current is switched off, preventing voltage spikes that could damage other components.
- Voltage Doubler Circuits: Can be used in circuits designed to effectively double the input voltage.
Sliding gate support roller
Ship or pick up from our office.
Sliding gate support roller
Sliding gate roller guides are essential components of sliding gates that facilitate smooth and controlled movement along a track or rail.
They help the gate stay aligned, preventing it from wobbling or coming off the track during operation. These guides are typically comprised of a bracket (often L-shaped) and one or more rollers, often made of nylon, that minimize friction and ensure quiet, efficient gate movement.
Key functions of sliding gate roller guides:
-
Smooth & Stable Movement:They ensure the gate slides smoothly along the track, preventing jerky movements and noise.
-
Alignment & Stability:They keep the gate aligned with the track, preventing it from wobbling or falling off.
-
Reduced Friction:The rollers minimize friction between the gate and the track, improving the gate's efficiency and lifespan.
-
Enhanced Durability:By reducing friction and stress on the gate and its components, they contribute to the longevity of the entire system.
Types of Sliding Gate Roller Guides:
-
L-Shaped Bracket with Rollers:This is a common type, featuring an L-shaped bracket that can be mounted on a post and nylon rollers that guide the gate.
-
Cantilever Gate Rollers:Specifically designed for cantilever gates (those that don't require a bottom track), these rollers provide support and smooth movement.
-
Adjustable Rollers:Some guides allow for horizontal adjustment of the roller position to accommodate different gate widths.
-
Flat Mount Wheels:Used when there's no need for a wheel cutout, these screw directly onto the bottom rail of the gate.
Materials and Construction:
-
Rollers:Typically made of nylon or other durable materials that can withstand wear and tear.
-
Brackets:Often made of steel (galvanized or stainless steel) for strength and durability.
Applications:
Sliding driveway gates, Security gates, Garden gates, Barn doors, Garage doors, Sheds, and Storage spaces.
In essence, sliding gate roller guides are critical for the proper functioning and longevity of sliding gates, ensuring smooth, reliable, and quiet operation.
Gate operator control board fuse
Ship or pick up from our office.
Gate operator control board fuse
A gate operator control board fuse is a critical safety component found on the circuit board of an automatic gate system. Its primary function is to protect the electrical components of the gate operator from damage caused by excessive current, such as a short circuit or an overload. Essentially, it acts as a sacrificial link in the electrical circuit. If the current flowing through the circuit exceeds a predetermined safe limit, the thin metal wire or strip inside the fuse melts and breaks the circuit. This prevents the surge of electricity from reaching and damaging more expensive and vital components on the control board or in the motor. Types and Characteristics Gate operator control board fuses come in various amperage ratings, typically ranging from 0.2 to 15 amps, depending on the specific gate operator model and its power requirements. Some common characteristics include:- Slow-Blow/Time-Delay Fuses: Many gate operators use "slow-blow" or "time-delay" fuses. These fuses are designed to tolerate brief, temporary current surges that often occur when motors start up without immediately blowing. They only interrupt the circuit if the overload persists for a longer duration.
- Physical Form: They can be found in various physical forms, including glass tube fuses (common in older models), blade-style automotive fuses, or sometimes as surface-mount fuses directly on the printed circuit board.
- Short Circuit: A direct path for current to flow, bypassing the normal resistance, causing a sudden and large surge.
- Overload: The gate motor or another component drawing more current than it's designed for, perhaps due to mechanical obstruction, a faulty motor, or issues with the gate's movement (e.g., binding hinges, gate dragging on the ground).
- Component Failure: A faulty component on the control board or within the gate operator system itself can cause an abnormal current draw, leading the fuse to blow.
- Power Surges: External power surges from the main electrical supply or lightning strikes can also cause fuses to blow.
- Disconnect Power: Always disconnect all power to the gate operator before attempting any inspection or repair. This includes both AC power and any battery backup systems.
- Locate the Fuse: The fuse is typically located directly on the main control board, often in a small holder or a clear cover. Refer to your gate operator's manual for its exact location.
- Inspect the Fuse:
- For glass tube fuses, you can often visually inspect the wire inside; if it's broken or discolored, the fuse is blown.
- For blade-style fuses, there might be a visible break in the metal strip, or you can use a multimeter set to continuity mode. A blown fuse will show no continuity.
- Replace the Fuse: If the fuse is blown, replace it with a new fuse of the exact same amperage (ampere) and voltage rating. Using a fuse with a higher rating can lead to damage to the control board or other components, as it won't blow when it should. Using a lower rating may cause the fuse to blow unnecessarily.
UHF Label
Ship or pick up from our office.
UHF Label
A UHF (Ultra-High Frequency) label access control system uses radio-frequency identification (RFID) technology operating in the ultra-high frequency range (typically 860-960 MHz) to manage and control access to specific areas, buildings, or resources. It's a touchless, automated system that offers long-range reading capabilities and the ability to identify multiple items simultaneously, making it highly efficient for various applications like vehicle access, personnel tracking in large facilities, and event management. 🛂 How it Works The core principle of a UHF label access control system relies on the communication between RFID tags (labels) and RFID readers. Here's a breakdown of the process:- RFID Tags (Labels): These are small electronic devices, often in the form of adhesive labels, cards, or embedded devices. They contain a microchip that stores unique identification data and an antenna. Most UHF tags used in access control are passive, meaning they don't have their own power source and rely on the energy emitted by the reader.
- RFID Reader: The reader emits radio waves, creating an electromagnetic field. When a UHF RFID tag enters this field, it absorbs energy from the waves, which powers its microchip.
- Data Transmission: Once activated, the tag modulates the waves to transmit its stored data (its unique ID) back to the reader.
- Data Processing and Verification: The reader captures and decodes this data, then sends it to a central access control system (often a computer with specialized software and a backend database). The system verifies the tag's unique ID against a list of authorized credentials and pre-defined access rules.
- Access Granting/Denial: If the tag is authorized, the system sends a signal to unlock a door, open a gate, or grant access. If not authorized, access is denied, and the system may trigger an alarm or log the attempted entry.
- Logging: The system typically records all entry and exit events, providing a detailed audit trail for security and management purposes.
- UHF RFID Tags/Labels: These are the physical identifiers worn by individuals or attached to vehicles/assets. They store the unique ID and are read by the system.
- UHF RFID Readers: These devices emit radio waves to power and read the data from the tags. They are strategically installed at entry/exit points (e.g., doorways, gates). Fixed readers are common for specific zones, while handheld readers offer flexibility for mobile applications like inventory or searching for tags.
- Antennas: Connected to the readers, antennas are responsible for transmitting and receiving the radio signals. The type and placement of antennas affect the read range and coverage area.
- Access Control Software/System: This is the "brain" of the system. It manages the database of authorized tags, processes the data received from readers, applies access rules, and controls the locking mechanisms. It often integrates with other security or building management systems.
- Backend Database: Stores all the information related to RFID tags, authorized users, access levels, and event logs.
- Locking Mechanisms: These are the physical devices controlled by the system, such as electronic door locks, gate barriers, or turnstiles.
- Long Read Range 📏: UHF systems can read tags from several meters away (typically 3-10 meters, and sometimes up to 25 meters or more), allowing for hands-free and rapid access, particularly useful for vehicles or large volumes of people.
- High-Speed Data Transmission and Multi-Tag Reading ⚡: They can read multiple tags simultaneously (often over 100 tags per second), significantly improving efficiency in high-traffic areas and during events.
- Enhanced Efficiency ⏱️: Automation of access eliminates manual checks, reduces queuing times, and frees up staff for other tasks.
- Improved Security 🔒: Each tag has a unique identifier, making it difficult to forge or duplicate. The system provides real-time monitoring and detailed audit trails, enhancing accountability and security. Integration with other systems like surveillance cameras can further bolster security.
- Touchless Operation 🖐️: The long read range enables touchless access, which is beneficial for hygiene, particularly in high-traffic areas or environments where physical contact should be minimized.
- Scalability 📈: UHF RFID systems can be easily scaled to accommodate a growing number of users and access points without compromising performance.
- Durability and Resistance 💪: UHF tags are often resistant to environmental factors like water, oil, and chemicals, and the data stored on their chips is protected. They can also be reused.
- Reduced Wear and Tear: As there's no physical contact with readers, the system components experience less wear and tear, leading to lower maintenance costs.
Card Holder
Ship or pick up from our office.
Card Holder
A UHF/RFID card holder is a specialized enclosure designed to hold and protect UHF (Ultra-High Frequency) RFID cards, often used for access control, vehicle identification, and logistics.
These holders typically consist of a durable material with a slot or pocket to securely accommodate the card, and may feature a mounting mechanism like suction cups for windshield attachment.
They enable convenient and reliable use of UHF RFID cards in various applications, such as parking systems, building access, and asset tracking, by providing a designated place for the card and facilitating easy scanning by RFID readers.
UHF Tag
Ship or pick up from our office.
UHF Tag
A UHF (Ultra-High Frequency) tag access control system is a security solution that uses radio frequency identification (RFID) technology operating in the ultra-high frequency range (typically 860-960 MHz) to control and monitor entry and exit of individuals or vehicles to restricted areas. 🛂 It's an automated system that identifies an individual or object with a unique RFID tag and, based on pre-defined permissions, grants or denies access. Unlike traditional barcode systems, UHF RFID doesn't require a direct line of sight between the tag and reader, allowing for longer read ranges and the ability to read multiple tags simultaneously. How It Works A UHF tag access control system generally consists of four main components:- UHF RFID Tags: These are small electronic devices containing a microchip and an antenna. The microchip stores data, such as a unique identifier or user information. Passive UHF tags, the most common type, are powered by the electromagnetic field emitted by the reader. Active tags have their own battery, enabling longer read ranges and continuous data transmission.
- UHF RFID Readers: These devices emit radio waves to create an electromagnetic field. When a UHF tag enters this field, it absorbs energy (for passive tags) and uses it to power its microchip. The tag then modulates the waves to transmit its stored data back to the reader. Readers can be fixed at entry points (like doors or gates) or handheld.
- Antennas: Integrated with the reader, antennas are responsible for transmitting and receiving the radio signals. Their design and placement are crucial for optimizing read performance and range.
- Access Control Software/Server: This is the "brain" of the system. The reader sends the decoded tag data to the software, which compares it against a database of authorized users and their assigned access levels. If the credentials match, the software sends a signal to unlock the door, open a gate, or trigger another access action. This software also logs all access events, providing an audit trail.
- Long Read Range: UHF systems can read tags from several meters away, making them ideal for applications like vehicle access control where you don't need to stop and present a card.
- High Read Speed and Multi-Tag Reading: They can quickly read multiple tags at once, which is beneficial in high-traffic areas or for tracking numerous assets simultaneously.
- Automation and Efficiency: Automated identification eliminates the need for manual checks, speeding up entry and exit processes.
- Enhanced Security: By identifying individuals and logging access events, these systems improve security and accountability. Features like encryption and unique IDs help prevent unauthorized access and cloning.
- Durability: UHF tags are often designed to be robust and can withstand various environmental conditions, making them suitable for outdoor or industrial use.
- Scalability: Systems can be easily expanded to cover more access points or accommodate a larger number of users.
- Vehicle Access Control: Automatically granting access to parking lots, gated communities, or corporate campuses without requiring drivers to stop and swipe a card.
- Building and Room Access: Controlling entry to offices, secure areas, or sensitive facilities for employees and authorized personnel.
- Event Management: Using RFID-enabled wristbands or badges for quick and efficient entry to concerts, theme parks, or VIP areas.
- Asset Tracking: While primarily for access, the same technology can track the movement of valuable assets within a controlled environment.
- Personnel Tracking: Monitoring the presence and movement of staff within a facility for safety or operational purposes.
- Interference: Performance can be affected by certain materials like metal and liquids in the environment, which can interfere with radio waves.
- Cost: Initial installation costs can be higher compared to simpler access control methods due to the specialized hardware and software.
- Regulatory Compliance: UHF frequencies are not globally harmonized, meaning system components must comply with regional radio regulations.
- Security Risks: While secure, like any digital system, there's a potential for sophisticated cloning or hacking attempts if not properly secured with encryption and robust protocols.
UHF Card
Ship or pick up from our office.
UHF Card
UHF (Ultra High Frequency) Card Access Control is a system that uses Ultra High Frequency Radio-Frequency Identification (UHF RFID) technology for managing and controlling access to various areas. Unlike traditional access control systems that require a close proximity tap or swipe, UHF systems leverage the longer read range of UHF RFID to provide hands-free, faster, and more efficient access. How it Works ⚙️ The core components of a UHF Card Access Control system are:- UHF Cards/Tags: These are typically cards, key fobs, or even vehicle tags embedded with a UHF RFID inlay. They contain a unique identification number or other encoded data.
- UHF Readers: These devices emit radio waves in the UHF frequency range (typically 860-960 MHz). When a UHF card/tag enters the reader's range, the tag is powered by the radio waves and transmits its unique data back to the reader.
- Antennas: Integrated within or connected to the readers, these are responsible for transmitting and receiving the radio signals.
- Access Control Software/System: This software receives the data from the reader, verifies the tag's credentials against a database, and then grants or denies access based on predefined rules. If access is granted, it sends a signal to unlock a door, open a gate, etc.
- Tag enters field: A person with a UHF card or a vehicle with a UHF tag approaches the reader.
- Reader transmits signal: The UHF reader continuously emits radio waves.
- Tag responds: The passive UHF tag, powered by the reader's signal, transmits its unique ID back.
- Data received and processed: The reader captures the tag's data and sends it to the access control system.
- Access granted/denied: The system verifies the credentials and, if authorized, activates the access point (e.g., opens a barrier). This entire process happens wirelessly and often within milliseconds.
- Long Read Range: Unlike Low Frequency (LF) and High Frequency (HF) RFID systems, UHF can read tags from several meters away (up to 10-15 meters or more depending on the setup). This allows for hands-free access, such as for vehicles entering a parking lot or individuals walking through a gate without stopping.
- High-Speed Data Transmission and Multiple Tag Reading: UHF readers can read many tags simultaneously and quickly (hundreds of tags per second). This is crucial for high-traffic areas, reducing bottlenecks and improving efficiency.
- Convenience and Efficiency: Users don't need to physically present or swipe a card, leading to a smoother and faster access experience. This is especially beneficial in applications like vehicle access, parking management, and large event entry.
- Enhanced Security: UHF tags are difficult to counterfeit, and the systems often incorporate encryption and password protection to prevent unauthorized access and data manipulation. Real-time tracking capabilities can also enhance security oversight.
- Scalability and Centralized Management: Cloud-based UHF access control platforms allow administrators to manage users, permissions, and access points remotely and in real-time, making it easy to scale for larger organizations or multiple locations.
- Durability and Cost-Effectiveness (Long Term): UHF components are generally robust and durable, leading to lower maintenance and replacement costs over time compared to traditional systems.
- Low Frequency (LF) RFID (125-134 kHz):
- Read Range: Very short (typically a few centimeters).
- Characteristics: Less susceptible to interference from metal and liquids.
- Common Uses: Animal identification, car immobilizers, older access control systems where close proximity is acceptable.
- High Frequency (HF) RFID (13.56 MHz):
- Read Range: Short (up to 1 meter).
- Characteristics: Good for secure data transfer and applications requiring closer interaction. Often used with Near Field Communication (NFC).
- Common Uses: Contactless payments (e.g., Apple Pay, Google Pay), smart cards for building access, public transport ticketing, library systems.
- Ultra High Frequency (UHF) RFID (860-960 MHz):
- Read Range: Long (several meters up to 15+ meters).
- Characteristics: Ideal for long-range, high-speed identification of multiple items. More susceptible to interference from metals and liquids than LF/HF, though specialized tags and antenna designs can mitigate this. The industry standard for passive UHF RFID is often referred to as RAIN RFID.
- Common Uses: Vehicle access control, inventory management, supply chain tracking, asset tracking, automated toll collection, large-scale personnel tracking.
Mercury Level Switch
Ship or pick up from our office.
Mercury Level Switch
A mercury level switch is a type of electrical switch that uses a small amount of liquid mercury to open or close an electrical circuit based on its position or the level of a liquid. Essentially, the mercury acts as a conductive bridge between electrical contacts. How it Works The core component of a mercury level switch is a sealed glass or metal capsule containing one or more electrical contacts and a small, free-moving drop of mercury. When the switch or the liquid it's monitoring changes its tilt or level:- Tilt Switches: Gravity pulls the mercury to the lowest point within the capsule. If the tilt is sufficient, the mercury will flow to connect two or more contacts, completing an electrical circuit. Tilting it in the opposite direction moves the mercury away, breaking the circuit.
- Float Switches: In liquid level applications, the mercury switch is often integrated with a float mechanism. As the liquid level rises or falls, the float moves, which in turn tilts the mercury switch, causing the mercury to connect or disconnect the contacts.
- Displacement Switches: Some designs use a "plunger" that dips into a pool of mercury, raising the mercury level to contact an electrode and complete the circuit.
- Thermostats: In older thermostats, they controlled heating and cooling systems.
- Sump Pumps: Used to automatically turn on the pump when water levels rise.
- Appliances: Found in washing machines (for lid switches and load balancing), chest freezers (for lid lights), and some gas appliances like ovens and water heaters (as flame sensors).
- Automotive Industry: Previously used for trunk lid lights, ride control, and anti-lock braking systems.
- Industrial Settings: Utilized in liquid level control and safety systems.
- Roll Sensing/Tip-over Warnings: For construction equipment or other vehicles operating on uneven terrain.
- Durability and Reliability: The sealed contacts prevent oxidation, leading to a long lifespan.
- Quiet Operation: No abrupt snapping of contacts.
- No Contact Erosion: Mercury's liquid nature prevents the wear and tear seen in mechanical contacts.
- Spark-Free: They don't produce sparks when making or breaking circuits, making them suitable for hazardous environments.
- Toxicity of Mercury: This is the primary and most significant disadvantage. Mercury is a highly toxic substance, posing serious environmental and health risks if released.
- Environmental Concerns: Improper disposal of mercury switches can lead to widespread contamination. Due to these concerns, the use of mercury switches has been largely phased out in many applications, especially in new products.
- Sensitivity to Gravity/Orientation: While an advantage for tilt sensing, it makes them unsuitable for portable or mobile devices where orientation changes or vibrations could cause false readings.
- Limited Functionality: Most mercury switches provide only a simple on/off function.
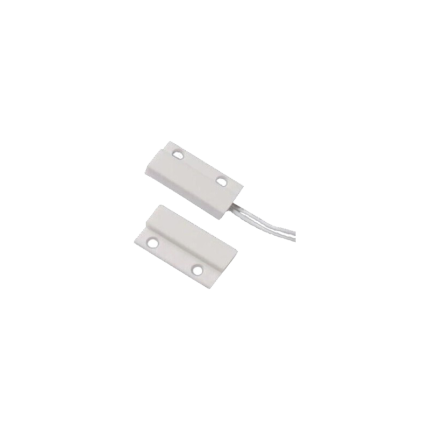
Magnetic Contact Switch – Wired
Ship or pick up from our office.
Magnetic Contact Switch
A magnetic contact switch, often simply called a magnetic contact or door/window sensor, is a simple yet highly effective security device that detects when a door, window, gate, or any movable barrier is opened or closed. How it Works: It consists of two main parts:- The Sensor Unit (with a Reed Switch): This part contains a reed switch. A reed switch is a small, hermetically sealed (airtight) glass capsule with two tiny, flexible magnetic metal reeds (or contacts) inside. These reeds are usually made of a ferromagnetic material. This sensor unit is typically mounted on the stationary part of the opening (e.g., the door frame, window frame, or gate post).
- The Magnet Unit: This part contains a small, permanent magnet. This unit is mounted on the moving part of the opening (e.g., the door itself, the window sash, or the gate panel).
- Closed Position (Circuit Complete): When the door/window/gate is closed, the magnet unit is in very close proximity to the sensor unit. The magnetic field from the permanent magnet pulls the two tiny reeds inside the glass capsule together, causing them to make electrical contact. This completes an electrical circuit, indicating that the opening is secured.
- Many common contacts are "Normally Open" (NO), meaning the circuit is open when the magnet is away and closes when the magnet is near.
- Some are "Normally Closed" (NC), meaning the circuit is closed when the magnet is near and opens when the magnet is away. This is very common in security systems, as an "open" circuit triggers an alarm.
- Opened Position (Circuit Broken/Changed): When the door/window/gate is opened, the magnet moves away from the reed switch. As the magnetic field weakens, the reeds spring back to their original position, breaking the electrical contact. This change in the circuit (from closed to open, or open to closed, depending on the type) signals the connected system (e.g., a car alarm, home security system, or gate control panel) that the opening has occurred.
- Security Systems (Homes, Businesses, Vehicles): This is the most prevalent use. Magnetic contacts are placed on:
- Doors and Windows: To detect unauthorized entry. When a door or window is opened, it triggers the alarm.
- Garage Doors/Overhead Doors: Larger, more robust magnetic contacts are used for garage doors.
- Gates: Used on pedestrian gates or even main driveway gates (sometimes in conjunction with the gate opener's own limit switches) to monitor their open/closed status for security purposes.
- Safes and Vaults: To detect if they have been opened.
- Vehicle Doors/Trunks/Hoods: While vehicles have internal sensors, magnetic contacts can be added for enhanced security on specific compartments or custom modifications.
- Access Control Systems: To monitor entry and exit points, log access events, or control other devices based on door status.
- Automation Systems: To trigger actions based on the status of a movable part. Examples include:
- Turning lights on/off when a door opens.
- Indicating when a cabinet door is ajar.
- Position sensing in industrial machinery.
- Appliance Safety: Some appliances use magnetic contacts to ensure a lid is closed or a guard is in place before operation.
- Surface Mount: Most common, easily screwed or adhered to the surface of the frame and door.
- Recessed/Flush Mount: Designed to be drilled into the frame and door for a more discreet, hidden installation.
- Heavy Duty/Overhead Door Contacts: Larger and more rugged, built for the heavier use and larger gaps often found with garage or industrial doors.
- Wired vs. Wireless:
- Wired: Physically connected to the alarm panel via wires, offering high reliability.
- Wireless: Contain a small battery and a radio transmitter to send signals wirelessly to the alarm panel, offering easier installation.