Access Control
Monitoring access to your commercial or residential property is an essential aspect of effective home security. There are many ways of safeguarding your property which require all types of access control methods. At Royal Gate, we have you covered with the best products and the latest technology options. We offer all methods of access control for complete integration into your existing or planned security system.
Effective access control doesn’t work in isolation; It needs to be integrated into your overall security system. Only then will you have proper control over who goes in and out of your property. You must always know who enters your home or business and we give you the tools for making it happen.
At Royal Gate, we have a robust offering of access control products and accessories. We offer a wide variety of digital access control keypads, card access systems, remote control transmitters, proximity access cards, telephone entry systems, fingerprint readers, and intercom systems. Browse our selection to find what is best for your security needs.
Above all, you want the peace of mind that is only afforded to those who have control over their access privileges, and we give you the tools to make it happen. Our state-of-the-art equipment puts your security in your hands in the way that it should be.
Video doorbell B104
Ship or pick up from our office.
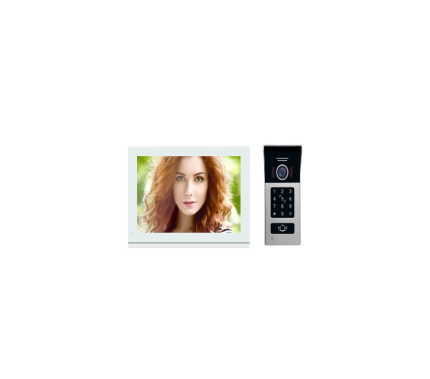
Video doorbell B104
The Video Doorbell B104 is an innovative intercom system that has been designed to meet the communication needs of modern residential buildings. With its advanced security features, ease of use, versatility, affordability, and quality assurance, this intercom system is an ideal communication solution for anyone looking for a reliable and cost-effective communication system. Place your order today and enjoy the benefits of a top-quality intercom system. This Video Doorbell System B104 comes with a 7” TFT Screen Monitor & FHD Camera and can be connected with only 4 wires between the house and outside of the property. 4 wires mean video core, audio core, 12V DC, and GND. It is for villa houses and supports extra CCTV cameras and alarm sensors. This KIT has a wide-view angle outdoor unit and a 7" indoor screen. The outdoor station and indoor monitor are 4-wire hard-wired. Built-in power supply and external power adaptor for optional. No matter what kind of house, you can find a suitable solution in Royal Gates!Video Doorbell B102
Ship or pick up from our office.
Video Doorbell B102
*Installing the smart video doorbell B102 using only one pair of wires.* Answer calls and unlock your door from your smartphone or other mobile devices
* Easily identify visitors on the large 7″ screen
* Store calls with no added fees using onboard memory
* Adding a microSD card to the on-site monitor increases call storage
* Watch recorded calls from the on-site master
Use Cases: The video doorbell B102 is a versatile security solution that can be used in a range of applications, including: 1. Private Residences: The intercom provides secure access control and entry monitoring for private residences, ensuring that only authorized persons gain access. 2. Commercial Properties: The video doorbell B102 intercom system is an ideal security solution for commercial properties such as offices, warehouses, and factories that require strict access control measures. 3. Retail Stores: The video doorbell B102 intercom can be used to control access to retail stores and prevent theft and unauthorized entry. 4. Gated Communities: The B102 video doorbell system is a valuable tool for gated communities that need enhanced security measures to protect their residents.Wireless Video Doorbell – B108
Ship or pick up from our office.
Wireless Video Doorbell - B108
The wireless video doorbell - B108 intercom system will connect to your smartphone and by using this amazing wireless video doorbell system, you not miss any visitor calls. You can open the automated gates/doors, from everywhere. The wireless video doorbell - B108 intercom system supports an RFID card and password to unlock function and the outdoor station with 2.0MP high resolution. The frequency of this wireless video intercom system is 800Mhz or 900Mhz, with a 100 meters range! The indoor monitor is a 7-inch touch screen and supports a max 32GB/SD card to store videos and pictures.Key selector -Key Automation EGS101
Ship or pick up from our office.
Key selector -Key Automation EGS101
The EGS101 is a gate/door opener key selector manufactured by KeyAutomation. It's designed for high-security residential and commercial properties and allows manual operation of automatic gates or doors using a physical key, according to KeyAutomation.TECHNICAL FEATURES
| Voltage | Vdc | Max 48 |
| Degree of protection | IP | 55 |
| Dimensions (L - D - H) | mm | 79 - 23 - 79 |
| Item | kg | 0,335 |
| Minimum operating temperature | °C | -20 |
| Max operating temperature | °C | +55 |
-
Function:Key selectors are designed to activate the door or gate opener's motor by completing an electrical circuit when the key is turned.
-
Mechanism:They typically involve a key cylinder that, when turned, activates a set of electrical contacts.
-
Applications:They are used in various settings, including residential, commercial, and industrial applications, such as garage doors, gates, and automatic doors.
-
Features:Some key selectors offer multiple functions, like automatic, lock, exit, and hold-open modes.
-
Types:They can be found as jamb key switches for garage doors or as more sophisticated selector switches for automatic doors with multiple functions.
Wireless Keypad Access Control -Key Automation EGKTR1
Ship or pick up from our office.
Wireless Keypad Access Control -Key Automation EGKTR1
*Wireless*Rain Shield Cover Included
*Finger Touch *Back Light *Protection degree: IP 55-
Wireless and Keyless Entry:The EGKTR1 enables keyless entry to properties by allowing users to enter a personalized code on the keypad to activate the gate or door.
-
Capacitive Touch Technology:This technology provides a responsive and durable touch surface, similar to a smartphone screen.
-
Compatibility:It's designed to work with Key Automation control units and receivers, making it a suitable addition to their access control systems.
-
Security Features:The EGKTR1 is a security device, providing controlled access to properties and can be programmed with multiple user codes.
-
Applications:It can be used for various applications, including commercial and residential buildings, educational institutions, and industrial facilities.
-
Installation and Programming:The keypad is designed for easy installation and programming, often with user-friendly instructions and procedures.
Keypad access control -Key Automation EGKTB1
Keypad access control -Key Automation EGKTB1
*BUS decoder powered *Rain Shield Cover Included *Touch *Protection degree: IP 55 *BacklightTECHNICAL FEATURES
| Duty cycle percentage | % | 100% |
| Voltage | Vac | 10-24 |
| Voltage | Vdc | 12-34 |
| AC Voltage Frequency | Hz | 50/60 |
| Nominal power | W | 0,25 |
| Peak power | W | 1,5 |
| Appliance isolation class | III | |
| Degree of protection | IP | 55 |
| Dimensions (L - D - H) | mm | 79 - 23 - 79 |
| Item | kg | 0,25 |
| Minimum operating temperature | °C | -10 |
| Max operating temperature | °C | +55 |
-
Access Control:The primary function of the EGKTB1 is to control access to a secured area.
-
Keypad Functionality:It allows users to enter a pre-set code using the keypad's buttons. This code is then verified by the connected security system.
-
Integration:It's designed to connect with a security system or control unit, often using a Wiegand protocol, to manage access permissions.
-
Security:Keypads offer a more secure alternative to traditional keys because they can be reprogrammed with new codes, and they eliminate the need to physically distribute keys.
-
Convenience:Keypads offer a convenient way to manage access, especially in situations where there are many users or frequent changes in access needs.
BUS Encoder -Key Automation EGKD2
Ship or pick up from our office.
BUS Encoder -Key Automation EGKD2
PRODUCT SHEET PDFTECHNICAL FEATURES
| Force | N | 93 |
| Duty cycle percentage | % | 100% |
| Voltage | Vac | 10-24 |
| Voltage | Vdc | 12-34 |
| AC Voltage Frequency | Hz | 50/60 |
| Nominal power | W | 0,2 |
| Peak power | W | 23 |
| Appliance isolation class | III | |
| Degree of protection | IP | 30 |
| Dimensions (L - D - H) | mm | 88 - 41 - 25 |
| Item | kg | 0,109 |
| Minimum operating temperature | °C | -10 |
| Max operating temperature | °C | +55 |
Doorbell SDB111
Ship or pick up from our office.
Doorbell SDB111
The "Doorbell SDB111" primarily refers to a wired doorbell system that operates on a 12-volt DC power supply. It's often associated with Royal Electronics Technology Center Co. and is commonly used for security access control in homes, offices, and other buildings. Here's a breakdown of its typical characteristics about the doorbell SDB111:- Wired System: The "12V" in its name signifies that it's a wired doorbell, meaning it connects to a power source via electrical wires. This usually involves a transformer that converts household voltage to 12V DC.
- Low Voltage: Like many doorbell systems, it operates on low voltage for safety.
- Functionality: Its primary function is to produce a chime sound (like a "ding-dong") when the doorbell button is pressed. It's often chosen for its durability and continuous function without needing battery replacements.
- Installation: These doorbells can be installed with screws or double-sided adhesive tape and typically come with wiring diagrams.
- Security Integration: They are considered a good security measure as they are external and can be integrated with other security systems.
- Access Control: The SDB111 is specifically mentioned in the context of access control systems, suggesting its use in managing entry to a property.
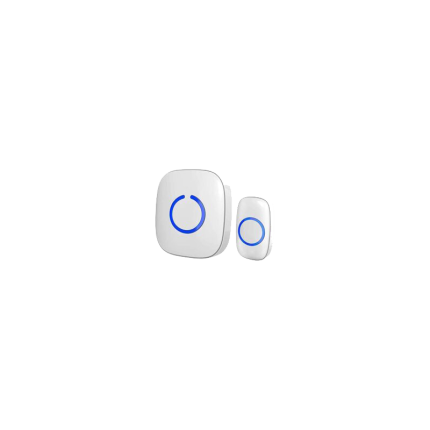
Wireless Doorbell
Ship or pick up from our office.
Wireless Doorbell
A wireless doorbell is a modern type of doorbell that operates without the need for physical wiring between the outdoor button and the indoor chime unit. Unlike traditional wired doorbells that rely on an electrical circuit, wireless doorbells use radio waves (or sometimes Wi-Fi or Bluetooth) to transmit a signal when the button is pressed. Here's a breakdown of its key components and how it works:- Transmitter (Doorbell Button): This is the part located outside your door that a visitor presses. It typically contains a small battery (though some "kinetic energy" versions generate power from the press itself) and sends a wireless signal when activated.
- Receiver (Chime Unit): This is the indoor component that produces the sound (chime or melody) when it receives the signal from the transmitter. Receivers can be battery-operated for portability or plug into a standard electrical outlet.
- When a visitor presses the doorbell button (transmitter), it sends a unique radio frequency (RF) signal.
- The signal travels wirelessly through the air.
- The receiver inside your home detects this signal.
- Upon receiving the signal, the receiver activates its chime or melody, alerting you to the visitor.
- Easy Installation: No need for complex wiring, drilling holes, or hiring an electrician. This makes them ideal for renters or anyone looking for a quick and simple setup.
- Flexibility and Portability: Since there are no wires, you can place the chime unit virtually anywhere in your home, and even move it around if needed. Many systems also allow for multiple receivers throughout a large house or property.
- Customization: Most wireless doorbells offer a variety of chime melodies and adjustable volume levels, allowing you to personalize the sound.
- Advanced Features (Smart Doorbells): Many modern wireless doorbells, often called "smart doorbells," integrate with Wi-Fi and offer additional features like:
- Video cameras: Allowing you to see who's at your door from your smartphone, even when you're not home.
- Two-way audio: Enabling you to speak with visitors remotely.
- Motion detection: Alerting you to activity outside your door.
- Smartphone notifications: Sending alerts to your phone when someone rings the bell or motion is detected.
- Integration with smart home systems: Connecting with other devices like smart lights or security systems.
- Enhanced Security: With features like video recording and remote monitoring, wireless doorbells can deter potential intruders and provide valuable evidence in case of an incident.
UHF Tag
Ship or pick up from our office.
UHF Tag
A UHF (Ultra-High Frequency) tag access control system is a security solution that uses radio frequency identification (RFID) technology operating in the ultra-high frequency range (typically 860-960 MHz) to control and monitor entry and exit of individuals or vehicles to restricted areas. 🛂 It's an automated system that identifies an individual or object with a unique RFID tag and, based on pre-defined permissions, grants or denies access. Unlike traditional barcode systems, UHF RFID doesn't require a direct line of sight between the tag and reader, allowing for longer read ranges and the ability to read multiple tags simultaneously. How It Works A UHF tag access control system generally consists of four main components:- UHF RFID Tags: These are small electronic devices containing a microchip and an antenna. The microchip stores data, such as a unique identifier or user information. Passive UHF tags, the most common type, are powered by the electromagnetic field emitted by the reader. Active tags have their own battery, enabling longer read ranges and continuous data transmission.
- UHF RFID Readers: These devices emit radio waves to create an electromagnetic field. When a UHF tag enters this field, it absorbs energy (for passive tags) and uses it to power its microchip. The tag then modulates the waves to transmit its stored data back to the reader. Readers can be fixed at entry points (like doors or gates) or handheld.
- Antennas: Integrated with the reader, antennas are responsible for transmitting and receiving the radio signals. Their design and placement are crucial for optimizing read performance and range.
- Access Control Software/Server: This is the "brain" of the system. The reader sends the decoded tag data to the software, which compares it against a database of authorized users and their assigned access levels. If the credentials match, the software sends a signal to unlock the door, open a gate, or trigger another access action. This software also logs all access events, providing an audit trail.
- Long Read Range: UHF systems can read tags from several meters away, making them ideal for applications like vehicle access control where you don't need to stop and present a card.
- High Read Speed and Multi-Tag Reading: They can quickly read multiple tags at once, which is beneficial in high-traffic areas or for tracking numerous assets simultaneously.
- Automation and Efficiency: Automated identification eliminates the need for manual checks, speeding up entry and exit processes.
- Enhanced Security: By identifying individuals and logging access events, these systems improve security and accountability. Features like encryption and unique IDs help prevent unauthorized access and cloning.
- Durability: UHF tags are often designed to be robust and can withstand various environmental conditions, making them suitable for outdoor or industrial use.
- Scalability: Systems can be easily expanded to cover more access points or accommodate a larger number of users.
- Vehicle Access Control: Automatically granting access to parking lots, gated communities, or corporate campuses without requiring drivers to stop and swipe a card.
- Building and Room Access: Controlling entry to offices, secure areas, or sensitive facilities for employees and authorized personnel.
- Event Management: Using RFID-enabled wristbands or badges for quick and efficient entry to concerts, theme parks, or VIP areas.
- Asset Tracking: While primarily for access, the same technology can track the movement of valuable assets within a controlled environment.
- Personnel Tracking: Monitoring the presence and movement of staff within a facility for safety or operational purposes.
- Interference: Performance can be affected by certain materials like metal and liquids in the environment, which can interfere with radio waves.
- Cost: Initial installation costs can be higher compared to simpler access control methods due to the specialized hardware and software.
- Regulatory Compliance: UHF frequencies are not globally harmonized, meaning system components must comply with regional radio regulations.
- Security Risks: While secure, like any digital system, there's a potential for sophisticated cloning or hacking attempts if not properly secured with encryption and robust protocols.
UHF Licence Plate
Ship or pick up from our office.
UHF Licence Plate
A UHF (Ultra High Frequency) Licence Plate access control system is a vehicle identification and access management solution that uses UHF RFID (Radio Frequency Identification) technology to automatically grant or deny entry to vehicles. Instead of relying on traditional license plate recognition (ANPR/LPR) which uses cameras to read visible plates, UHF systems use RFID tags, often in the form of stickers or cards, affixed to vehicles. 🚗 When a vehicle with a registered UHF RFID tag approaches an access point (like a gate or barrier), a UHF reader emits radio waves. The tag, powered by these waves, transmits its unique identification data back to the reader. This data is then sent to an access control system which verifies the vehicle's authorization. If authorized, the system triggers the gate to open, allowing for fast, hands-free, and seamless entry and exit. This technology is widely used in places requiring efficient and secure vehicle flow, such as:- Gated communities 🏡
- Parking facilities (corporate, commercial, residential) 🅿️
- Industrial sites and logistics hubs 🏭
- Toll roads 🛣️
- UHF RFID Tags: These are small, passive (battery-less) or semi-active devices that contain a microchip storing a unique identification number and an antenna. They are typically affixed to the vehicle's windshield or license plate. When exposed to radio waves from a reader, the tag's antenna collects energy, powering the microchip to transmit its data.
- UHF RFID Readers: These devices are installed at access points (e.g., gate entrances) and emit radio waves to detect and read the RFID tags on approaching vehicles. They have antennas to send and receive signals, and a processor to decode the data from the tags. UHF readers typically have a longer read range (up to 10-12 meters or more) compared to other RFID frequencies, allowing vehicles to pass without fully stopping.
- Access Control System (Software/Controller): This is the "brain" of the system. The reader sends the tag's ID number to this system. The access control software then compares this ID with its database of authorized vehicles. Based on pre-defined criteria (e.g., specific times of day, authorized user groups), it determines whether to grant or deny access.
- Barrier/Gate System: If access is granted by the control system, a signal is sent to the physical barrier (like a boom gate or sliding gate), which opens to allow the vehicle to pass.
- Speed and Efficiency 🚀: Vehicles don't need to stop or roll down windows, significantly reducing traffic congestion, especially during peak hours. This provides a "frictionless" entry experience.
- Long Read Range 📏: UHF RFID allows for detection from several meters away, enabling quick processing of vehicles even at higher speeds.
- Reliability in Diverse Conditions 🌧️☀️: Unlike optical ANPR systems that can be affected by dirt, rain, snow, or poor lighting, UHF RFID tags are generally more robust and less susceptible to environmental factors.
- Enhanced Security 🔒: RFID tags are difficult to duplicate or tamper with, offering a higher level of security than some other methods. The system also logs all entries and exits, providing a clear audit trail.
- Reduced Operational Costs 💰: Automation minimizes the need for manual gate attendants, leading to lower labor costs over time. There's also no need for physical cards or key fobs that can be lost or damaged, saving on replacement costs.
- Integration Capabilities 🔗: These systems can often integrate seamlessly with other security and management platforms, such as visitor management systems, surveillance cameras, and parking management software, for a comprehensive solution.
UHF Label
Ship or pick up from our office.
UHF Label
A UHF (Ultra-High Frequency) label access control system uses radio-frequency identification (RFID) technology operating in the ultra-high frequency range (typically 860-960 MHz) to manage and control access to specific areas, buildings, or resources. It's a touchless, automated system that offers long-range reading capabilities and the ability to identify multiple items simultaneously, making it highly efficient for various applications like vehicle access, personnel tracking in large facilities, and event management. 🛂 How it Works The core principle of a UHF label access control system relies on the communication between RFID tags (labels) and RFID readers. Here's a breakdown of the process:- RFID Tags (Labels): These are small electronic devices, often in the form of adhesive labels, cards, or embedded devices. They contain a microchip that stores unique identification data and an antenna. Most UHF tags used in access control are passive, meaning they don't have their own power source and rely on the energy emitted by the reader.
- RFID Reader: The reader emits radio waves, creating an electromagnetic field. When a UHF RFID tag enters this field, it absorbs energy from the waves, which powers its microchip.
- Data Transmission: Once activated, the tag modulates the waves to transmit its stored data (its unique ID) back to the reader.
- Data Processing and Verification: The reader captures and decodes this data, then sends it to a central access control system (often a computer with specialized software and a backend database). The system verifies the tag's unique ID against a list of authorized credentials and pre-defined access rules.
- Access Granting/Denial: If the tag is authorized, the system sends a signal to unlock a door, open a gate, or grant access. If not authorized, access is denied, and the system may trigger an alarm or log the attempted entry.
- Logging: The system typically records all entry and exit events, providing a detailed audit trail for security and management purposes.
- UHF RFID Tags/Labels: These are the physical identifiers worn by individuals or attached to vehicles/assets. They store the unique ID and are read by the system.
- UHF RFID Readers: These devices emit radio waves to power and read the data from the tags. They are strategically installed at entry/exit points (e.g., doorways, gates). Fixed readers are common for specific zones, while handheld readers offer flexibility for mobile applications like inventory or searching for tags.
- Antennas: Connected to the readers, antennas are responsible for transmitting and receiving the radio signals. The type and placement of antennas affect the read range and coverage area.
- Access Control Software/System: This is the "brain" of the system. It manages the database of authorized tags, processes the data received from readers, applies access rules, and controls the locking mechanisms. It often integrates with other security or building management systems.
- Backend Database: Stores all the information related to RFID tags, authorized users, access levels, and event logs.
- Locking Mechanisms: These are the physical devices controlled by the system, such as electronic door locks, gate barriers, or turnstiles.
- Long Read Range 📏: UHF systems can read tags from several meters away (typically 3-10 meters, and sometimes up to 25 meters or more), allowing for hands-free and rapid access, particularly useful for vehicles or large volumes of people.
- High-Speed Data Transmission and Multi-Tag Reading ⚡: They can read multiple tags simultaneously (often over 100 tags per second), significantly improving efficiency in high-traffic areas and during events.
- Enhanced Efficiency ⏱️: Automation of access eliminates manual checks, reduces queuing times, and frees up staff for other tasks.
- Improved Security 🔒: Each tag has a unique identifier, making it difficult to forge or duplicate. The system provides real-time monitoring and detailed audit trails, enhancing accountability and security. Integration with other systems like surveillance cameras can further bolster security.
- Touchless Operation 🖐️: The long read range enables touchless access, which is beneficial for hygiene, particularly in high-traffic areas or environments where physical contact should be minimized.
- Scalability 📈: UHF RFID systems can be easily scaled to accommodate a growing number of users and access points without compromising performance.
- Durability and Resistance 💪: UHF tags are often resistant to environmental factors like water, oil, and chemicals, and the data stored on their chips is protected. They can also be reused.
- Reduced Wear and Tear: As there's no physical contact with readers, the system components experience less wear and tear, leading to lower maintenance costs.