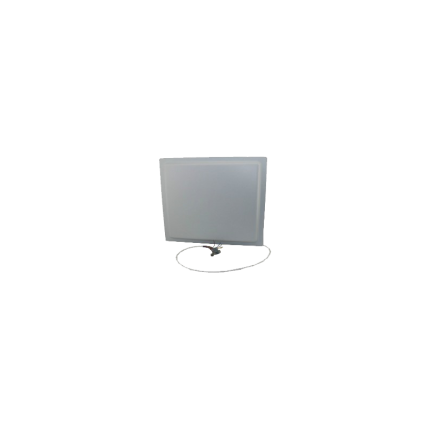
Access Control
UHF Card
Ship or pick up from our office.
UHF Card
UHF (Ultra High Frequency) Card Access Control is a system that uses Ultra High Frequency Radio-Frequency Identification (UHF RFID) technology for managing and controlling access to various areas. Unlike traditional access control systems that require a close proximity tap or swipe, UHF systems leverage the longer read range of UHF RFID to provide hands-free, faster, and more efficient access. How it Works ⚙️ The core components of a UHF Card Access Control system are:- UHF Cards/Tags: These are typically cards, key fobs, or even vehicle tags embedded with a UHF RFID inlay. They contain a unique identification number or other encoded data.
- UHF Readers: These devices emit radio waves in the UHF frequency range (typically 860-960 MHz). When a UHF card/tag enters the reader's range, the tag is powered by the radio waves and transmits its unique data back to the reader.
- Antennas: Integrated within or connected to the readers, these are responsible for transmitting and receiving the radio signals.
- Access Control Software/System: This software receives the data from the reader, verifies the tag's credentials against a database, and then grants or denies access based on predefined rules. If access is granted, it sends a signal to unlock a door, open a gate, etc.
- Tag enters field: A person with a UHF card or a vehicle with a UHF tag approaches the reader.
- Reader transmits signal: The UHF reader continuously emits radio waves.
- Tag responds: The passive UHF tag, powered by the reader's signal, transmits its unique ID back.
- Data received and processed: The reader captures the tag's data and sends it to the access control system.
- Access granted/denied: The system verifies the credentials and, if authorized, activates the access point (e.g., opens a barrier). This entire process happens wirelessly and often within milliseconds.
- Long Read Range: Unlike Low Frequency (LF) and High Frequency (HF) RFID systems, UHF can read tags from several meters away (up to 10-15 meters or more depending on the setup). This allows for hands-free access, such as for vehicles entering a parking lot or individuals walking through a gate without stopping.
- High-Speed Data Transmission and Multiple Tag Reading: UHF readers can read many tags simultaneously and quickly (hundreds of tags per second). This is crucial for high-traffic areas, reducing bottlenecks and improving efficiency.
- Convenience and Efficiency: Users don't need to physically present or swipe a card, leading to a smoother and faster access experience. This is especially beneficial in applications like vehicle access, parking management, and large event entry.
- Enhanced Security: UHF tags are difficult to counterfeit, and the systems often incorporate encryption and password protection to prevent unauthorized access and data manipulation. Real-time tracking capabilities can also enhance security oversight.
- Scalability and Centralized Management: Cloud-based UHF access control platforms allow administrators to manage users, permissions, and access points remotely and in real-time, making it easy to scale for larger organizations or multiple locations.
- Durability and Cost-Effectiveness (Long Term): UHF components are generally robust and durable, leading to lower maintenance and replacement costs over time compared to traditional systems.
- Low Frequency (LF) RFID (125-134 kHz):
- Read Range: Very short (typically a few centimeters).
- Characteristics: Less susceptible to interference from metal and liquids.
- Common Uses: Animal identification, car immobilizers, older access control systems where close proximity is acceptable.
- High Frequency (HF) RFID (13.56 MHz):
- Read Range: Short (up to 1 meter).
- Characteristics: Good for secure data transfer and applications requiring closer interaction. Often used with Near Field Communication (NFC).
- Common Uses: Contactless payments (e.g., Apple Pay, Google Pay), smart cards for building access, public transport ticketing, library systems.
- Ultra High Frequency (UHF) RFID (860-960 MHz):
- Read Range: Long (several meters up to 15+ meters).
- Characteristics: Ideal for long-range, high-speed identification of multiple items. More susceptible to interference from metals and liquids than LF/HF, though specialized tags and antenna designs can mitigate this. The industry standard for passive UHF RFID is often referred to as RAIN RFID.
- Common Uses: Vehicle access control, inventory management, supply chain tracking, asset tracking, automated toll collection, large-scale personnel tracking.
UHF Gate Controller
Ship or pick up from our office.
UHF Gate Controller
A UHF Gate Controller is a system that uses Ultra-High Frequency (UHF) Radio Frequency Identification (RFID) technology to manage and control access through a gate or designated entry/exit point. It typically consists of a UHF RFID reader, antennas, and a control unit that processes the data and triggers the gate mechanism. It's designed for automated, hands-free identification and tracking of people or objects equipped with UHF RFID tags, offering a longer read range and faster processing compared to other RFID frequencies. How it Works The fundamental principle of a UHF Gate Controller relies on the interaction between a UHF RFID reader and UHF RFID tags. Here's a breakdown:- UHF RFID Reader and Antennas: The gate controller incorporates a UHF RFID reader connected to one or more antennas. These antennas emit radio waves in the UHF frequency band (typically 860-960 MHz).
- RFID Tags: People, vehicles, or items needing access are equipped with UHF RFID tags. These tags contain a microchip that stores data (like a unique ID) and an antenna. Passive UHF tags, which are common in these systems, do not have their own power source; they draw power from the radio waves emitted by the reader.
- Data Exchange: When a tagged item or person enters the read range of the gate's antennas, the RFID tag is energized by the reader's radio waves. The tag then modulates these waves to send its stored data back to the reader.
- Data Processing and Control: The UHF RFID reader receives the tag's data and sends it to a control unit (often an integrated part of the gate system or a separate access controller). This control unit verifies the tag's information against a database of authorized entries.
- Gate Activation: If the tag is authorized, the control unit sends a signal to open or enable the gate (e.g., a barrier arm, turnstile, or door lock). If the tag is unauthorized, access is denied, and an alarm might be triggered.
- Directional Detection and Anti-Collision: Advanced UHF gate controllers can detect the direction of movement (e.g., entering or exiting) and employ anti-collision algorithms to read multiple tags simultaneously, even in high-traffic scenarios. Some systems use additional sensors (like infrared) to improve accuracy and prevent "tailgating."
- Long Read Range: Typically able to read tags from several meters away, allowing for "hands-free" and "drive-through" access.
- High Reading Speed: Can quickly identify multiple tags in motion, reducing bottlenecks.
- Anti-Collision: Algorithms that allow the reader to differentiate and read multiple tags present in the field at the same time.
- Directional Sensing: Ability to determine if an item or person is entering or exiting the controlled area.
- Integration Capabilities: Often connect with other security or management systems via interfaces like Ethernet, RS232, RS485, or Wi-Fi.
- Robust Design: Many are built for industrial or outdoor environments, with resistance to dust and water.
- Vehicle Access Control: Managing entry and exit for parking lots, gated communities, corporate campuses, and toll roads. Vehicles can have tags on windshields, allowing for seamless, hands-free access.
- People Access Control: Controlling access to buildings, restricted areas, and for time and attendance tracking in offices, universities, hospitals, and event venues.
- Logistics and Warehouse Management: Monitoring the flow of goods, pallets, and containers in and out of warehouses, distribution centers, and production lines for inventory management, asset tracking, and theft prevention.
- Retail: Used at store exits for Electronic Article Surveillance (EAS) to prevent shoplifting, and for inventory tracking as items move in and out of the backroom.
- Libraries and Document Management: Tracking books, documents, and other assets as they enter or leave a facility.
- Manufacturing: Monitoring materials and finished products on production lines and at factory entrances/exits.
GSM Gate Controller RTU5024
Ship or pick up from our office.
GSM Gate Controller RTU5024
The GSM Gate Controller RTU5024 is a device that allows you to control gates, doors, and other electrical equipment remotely using a mobile phone. It functions as a GSM relay switch, meaning it utilizes the Global System for Mobile Communications (GSM) network to receive commands and activate a built-in relay. How it Works ⚙️ The RTU5024 operates by accepting calls from authorized phone numbers. When an authorized user dials the SIM card number installed in the RTU5024, the device recognizes the caller ID, rejects the call (so there are no call charges), and then activates its relay. This relay can be connected to the mechanism of a gate, door, or other machinery, effectively opening, closing, or switching it on/off. Users can also manage the device and its authorized numbers via SMS commands or a dedicated smartphone app. Key Features ✨- No Call Charges: The device rejects calls from authorized numbers after the first ring, meaning there are no charges incurred for operating it via phone call.
- Caller ID Authentication: It uses caller ID for identification, ensuring only authorized numbers can control the device. Unknown callers are ignored.
- Remote Operation: Can be operated from anywhere with GSM network coverage, with no distance limitations.
- User Management: Authorized phone numbers (typically up to 200, though some versions support more) can be added or removed via SMS text commands or through a smartphone app.
- Relay Output: Features one output with a relay rating (e.g., 3A/240VAC) for connecting to various switches or machines.
- SMS Confirmation: The device can be configured to send an SMS confirmation to the owner or authorized number after a relay action.
- Programmable Relay Time: The duration for which the relay remains open or closed is often programmable.
- Quad-band GSM: Works on universal GSM frequencies (850/900/1800/1900MHz), making it compatible with most GSM networks worldwide. Some versions also support 3G or 4G.
- Smartphone App: Available with companion apps for Android and iOS for easier configuration and control.
- No Physical Remote Needed: Eliminates the need for multiple physical remote controls or keys for different users.
- Access Control: Remotely opening/closing swing/sliding gates, garage doors, shutters, and pedestrian doors for residential, commercial, or industrial properties.
- Car Parking Systems: Controlling barriers and access for parking lots.
- Remote Equipment Control: Switching on/off various remote equipment like street lights, motors, pumps, fans, inverters, PLCs, and air conditioners.
- Agriculture: Remote control of agricultural pumps and irrigation systems.
- Business: Managing electronic boxes, billboards, and LED signs remotely.
- Security: Can be integrated into basic security systems for remote monitoring or activation of alarms.
Infrared Card
Ship or pick up from our office.
Infrared Card
An Infrared Card, also known as an infrared detection card or laser viewing card, is a tool used to visualize infrared light, typically from lasers or other sources, by converting it into a visible light display. It's a simple, low-cost way to check for the presence and position of infrared beams, making it useful for alignment, safety, and diagnostic purposes.
Here's a more detailed explanation:
What it does:
-
Converts invisible IR light to visible light:The card contains a material, often phosphorescent, that absorbs infrared radiation and then emits visible light when stimulated.
-
Indicates presence and location:The illuminated spot on the card shows where the infrared beam is hitting, making it easy to see the beam's path and focal point.
-
Used for various applications:Infrared cards are used for aligning lasers, checking for infrared light leakage, visualizing infrared beams from various sources, and ensuring safety by detecting potentially harmful IR radiation.
Fingerprint Access Control
Ship or pick up from our office.
Fingerprint Access Control
A fingerprint access control system is a security system that uses an individual's unique fingerprint to grant or deny access to a physical space (like a building or a room) or a digital system. It's a type of biometric access control, which relies on distinct biological traits for identification. How it Works The process generally involves two main steps:- Enrollment: When a user is first set up in the system, a fingerprint scanner captures an image of their fingerprint. This image is then converted into a digital template (a mathematical code, not an actual image) and securely stored in a database. This template represents the unique characteristics of that person's fingerprint, such as ridge endings and bifurcations.
- Verification: When someone tries to gain access, they place their finger on the scanner again. The system captures a new image, converts it into a template, and then compares it to the stored template in the database. If there's a match, access is granted; otherwise, it's denied. This entire process is typically very fast.
- Fingerprint Reader/Scanner: The device that captures the fingerprint image.
- Communication Network: To transmit the captured data to the database.
- Database: Where the digital fingerprint templates are stored.
- Management Software: For administering users, permissions, and logging access events.
- Electronic Door Locks: Locks that are controlled by the system, opening when access is granted.
- Power Supply: To power all the system components.
- Enhanced Security: Fingerprints are unique to each individual and are extremely difficult to replicate or steal, making them more secure than traditional keys, cards, or PINs.
- Convenience: Users don't need to carry keys or remember codes, as their fingerprint is always with them.
- Improved Accountability: Every access event is tied to a specific individual, creating clear and accurate audit trails.
- Reduced Risk of Lost/Stolen Credentials: There are no physical keys or cards to be lost, stolen, or shared.
- Cost-Effective in the Long Run: While there might be an initial investment, it can save money by eliminating the need for replacing lost cards or rekeying locks.
- Physical Contact Required: Most fingerprint scanners require direct contact, which can be a hygiene concern and may not work if fingers are dirty, wet, or injured.
- Potential for Recognition Issues: Scars, calluses, or even minor cuts can sometimes make it difficult for the system to recognize a fingerprint, leading to false rejections.
- Enrollment Time: Registering each user's fingerprint can be time-consuming in large organizations.
- Spoofing Concerns: While difficult, advanced techniques could potentially "spoof" a fingerprint. Modern systems often include "liveness detection" to counter this.
- Not Ideal for Visitors: It's not practical to enroll temporary visitors for short-term access.
- Optical Scanners: Capture a visual image of the fingerprint using light.
- Capacitive Scanners: Use electrical current to create an image of the fingerprint's ridges and valleys.
- Ultrasonic Scanners: Use sound waves to create a 3D map of the fingerprint.
- Thermal Scanners: Detect temperature differences between the ridges and valleys.
- Touchless Fingerprint Readers: Some newer systems allow for contactless scanning, often using 3D imaging of multiple fingers.
Wireless Keypad Access Control – ALEKO LM172
Ship or pick up from our office.
Wireless Keypad Access Control – ALEKO LM172
-Rain Shield Cover included *Backlight *433 MHz The ALEKO LM172 is a wireless keypad access control system primarily designed for use with ALEKO brand swing and sliding gate openers. It provides a secure and convenient way to control access to a property by requiring users to enter a programmable 6-digit code. Key Features & Specifications- Wireless Operation: It's completely wireless, eliminating the need for electrical connections to the gate opener. It operates on 3 AAA batteries.
- Frequency: It uses a 433.92 MHz frequency for communication with compatible gate openers.
- Security: Enhances security by restricting access to authorized individuals who know the programmable 6-digit code, reducing reliance on traditional remote controls.
- Durability: Features a rugged metal construction designed to withstand various weather conditions. Some listings mention heavy-duty iron construction.
- Visibility: Equipped with backlit keys for easy use in low-light conditions.
- Compact Design: Has a relatively compact profile (approx. 3.5"L x 3.25"W x 1"D or 4" x 3" x 3").
- Range: Offers a typical operating range of up to 32 feet (10 meters) from the gate opener's receiver. It's recommended to install it within 5 meters (16 feet) of the control box on the same side of the driveway to avoid interference.
- Installation: Designed for easy installation, typically mounted with screws. It can be buried in the ground or fixed on the ground with a compatible mounting post.
- ALEKO Swing Gate Openers: AS/GG Series (e.g., AS450, AS600, AS650, AS900, AS1200, AS1300, AS1700 models).
- ALEKO Sliding Gate Openers: AR/AC Series (e.g., AR900, AR1300, AR1800, AR2200, AR2700, AR5700, AC1300, AC1800, AC2200, AC2700, AC5700 models).
- LockMaster Gate Openers: LM901 and LM902 Swing Gate Openers.
- DSC DSR SCG/SFG (H model only) Sliding Gate Openers: Purchased after July 2011.
- Powering on the control board and ensuring it's in standby mode.
- Pressing a "LEARN" button on the control board.
- Pressing the "OK" button on the LM172 keypad to link it with the gate opener.
- Once successfully learned, the control board's LED will indicate confirmation.
Card Holder
Ship or pick up from our office.
Card Holder
A UHF/RFID card holder is a specialized enclosure designed to hold and protect UHF (Ultra-High Frequency) RFID cards, often used for access control, vehicle identification, and logistics.
These holders typically consist of a durable material with a slot or pocket to securely accommodate the card, and may feature a mounting mechanism like suction cups for windshield attachment.
They enable convenient and reliable use of UHF RFID cards in various applications, such as parking systems, building access, and asset tracking, by providing a designated place for the card and facilitating easy scanning by RFID readers.
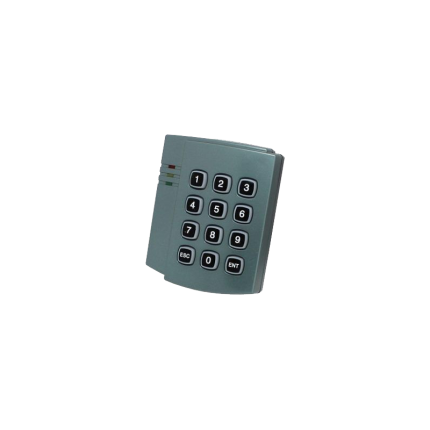
Keypad access control K100SC104
Ship or pick up from our office.
Keypad access control K100SC104
(Recommended for indoor usage) *Rain Shield Cover is included *Waterproof Version *EM/ID card/tag reader *Backlight *500 User *DC 12 VRFID Tag Access Control
Ship or pick up from our office.
RFID Tag Access Control
RFID Tag Access Control is a system that uses Radio Frequency Identification (RFID) technology to manage and control access to physical spaces or logical systems. It allows only authorized individuals or items to enter secure areas by wirelessly reading data stored on RFID tags. Think of it as a modern, electronic key system where your "key" is an RFID tag (like a card or key fob) and the "lock" is an RFID reader. How it Works ⚙️ The fundamental principle is straightforward:- RFID Tag/Credential: Each authorized individual or item is assigned an RFID tag. This tag contains a microchip that stores a unique identification code and an antenna.
- RFID Reader: A reader (also called an interrogator) is installed at the access point (e.g., a door, gate, or turnstile). The reader emits radio waves.
- Communication: When an RFID tag comes within range of the reader's radio waves, the tag's antenna captures energy from the reader's signal (for passive tags) or uses its own power source (for active tags) to activate its microchip. The tag then transmits its unique data back to the reader.
- Data Processing: The reader decodes the information from the tag and sends it to a central access control software or system.
- Authentication and Decision: The software compares the tag's unique ID with a database of authorized users and their assigned permissions. If the ID is valid and the user has permission to access that specific area at that time, the system sends a signal to unlock the door, open the gate, or grant access. If not, access is denied.
- Logging: The system typically logs every access attempt (both granted and denied), providing an audit trail for security monitoring and compliance.
- RFID Tag Access Controls/Credentials: These are the physical devices carried by users. They come in various forms, such as:
- Cards: Similar to credit cards, commonly used for employee badges or hotel key cards.
- Key Fobs: Small, convenient devices attached to keychains.
- Wristbands: Often used in recreational facilities or for events.
- Stickers/Labels: Can be affixed to items or vehicles.
- Mobile Credentials: Increasingly, smartphones can act as RFID tags through NFC (Near Field Communication), a subset of HF RFID.
- RFID Readers: Devices that emit radio waves to energize and read data from RFID tags. They can be fixed (at entry points) or mobile (handheld scanners).
- Antennas: Integral to the reader (or external), they transmit and receive radio signals to and from the tags. The antenna design influences the read range and reliability.
- Access Control Software/Management System: The "brain" of the system. This software manages user databases, assigns access permissions, logs events, and allows administrators to configure and monitor the system remotely.
- Access Control Panel/Controller: Hardware that connects the readers to the central software, processing data and controlling the locking mechanisms.
- Passive RFID Tags:
- Do not have an internal power source.
- They draw power from the radio waves emitted by the reader to operate.
- Are generally smaller, less expensive, and require no maintenance.
- Have a shorter read range (a few centimeters to a few feet).
- Most commonly used in access control for cards and key fobs.
- Active RFID Tags:
- Have their own internal power source (battery).
- Can transmit data over longer distances (up to several hundred meters) and at regular intervals.
- Are larger and more expensive.
- Often used for long-range applications like vehicle tracking or asset management.
- Semi-Passive RFID Tags (Battery-Assisted Passive - BAP):
- Contain a battery to power the microchip, but still rely on the reader's signal to initiate communication.
- Offer better read range and performance than passive tags, without continuously transmitting like active tags.
- Low Frequency (LF) RFID (125-134 kHz):
- Short read range (1-10 cm).
- Less susceptible to interference from metal and water.
- Common in traditional access control systems.
- High Frequency (HF) RFID (13.56 MHz):
- Moderate read range (10 cm-1 meter).
- Widely used for access control, ticketing, and Near Field Communication (NFC) applications (like smartphone taps).
- Ultra-High Frequency (UHF) RFID (300 MHz-3 GHz, often 860-960 MHz for RAIN RFID):
- Long read range (up to 12 meters).
- More susceptible to interference from liquids and metals.
- Used in applications requiring longer read distances, such as vehicle access control or large-scale inventory tracking.
RFID Card Access Control
Ship or pick up from our office.
RFID Card Access Control
RFID card access control is a system that uses Radio Frequency Identification (RFID) technology to manage and control access to physical spaces. It provides a secure and convenient way to grant or deny entry to authorized individuals, replacing traditional keys or swipe cards. This system works by wirelessly communicating between an RFID card (or tag) and an RFID reader. How it Works- RFID Card (Tag): Each authorized individual carries an RFID card, key fob, or even a smartphone with an embedded RFID chip. This chip contains a unique identification code and sometimes other encrypted data.
- RFID Reader: Readers are installed at entry points (doors, gates, elevators, etc.). They constantly emit a radio frequency field.
- Communication: When an RFID card enters the reader's field, the card's antenna captures energy from the reader's signal. This energizes the microchip on the card, allowing it to transmit its unique data back to the reader.
- Data Verification: The RFID reader decodes the information from the card and sends it to a central access control server or control panel. This server compares the card's data with a secure database of authorized users and their access permissions.
- Access Grant/Denial: If the credentials match an authorized profile, the system sends a signal to an electronic lock mechanism, allowing entry. If not, access is denied. This entire process typically happens in milliseconds.
- Audit Trail: The system also records detailed access information, including the time, date, and specific access point used, providing a valuable audit trail for security purposes.
- RFID Cards/Tags: These are the credentials held by users, typically in the form of plastic cards, key fobs, or even integrated into mobile devices. They contain a microchip and an antenna.
- RFID Readers (Interrogators): Devices installed at entry points that emit radio waves to communicate with the tags and read their data.
- Access Control Panel/Server: This is the "brain" of the system. It receives data from the readers, verifies user credentials against a database, and controls the electronic locks. It can be cloud-based or local.
- Electronic Locks: Devices that secure the entry points and are controlled by the access control system (e.g., magnetic locks, electric strikes).
- Access Control Software: Software used to manage user profiles, set access levels, monitor events, and generate reports.
- Passive RFID Tags: Most common for access control. They don't have an internal battery and are powered by the electromagnetic field emitted by the reader. They have a shorter read range (a few centimeters to a meter).
- Active RFID Tags: These tags have their own power source (battery), allowing for a much longer read range (up to several hundred meters) and the ability to broadcast signals periodically. They are typically more expensive.
- Semi-Passive RFID Tags: These tags have a battery to power the chip but only transmit data when activated by a reader's signal, offering improved sensitivity and performance over passive tags.
- Convenience: Offers contactless and keyless entry, making it fast and easy for users to gain access. Cards can often be read from inside a wallet or bag.
- Enhanced Security: Provides unique identification and can utilize encrypted communication, making tags difficult to duplicate. Lost cards can be immediately deactivated, preventing unauthorized use.
- Efficiency: Streamlines entry and exit processes, reducing wait times, especially in high-traffic areas.
- Flexibility & Scalability: Easily allows for adjusting access permissions for different users, areas, or time frames. Systems can be expanded or modified as needs change.
- Integration: Can be integrated with other security systems like CCTV, alarms, and time attendance systems for comprehensive security management.
- Audit Trails: Provides real-time tracking of who enters and exits, offering valuable data for security monitoring and incident investigation.
- Durability: RFID components generally experience less wear and tear compared to traditional mechanical locks or swipe card systems.
- Skimming: In theory, unauthorized readers could attempt to read card information if they get close enough, though modern RFID cards often use one-time codes and encryption to mitigate this risk.
- Cloning: If the security protocols are weak, an RFID card's information could potentially be cloned.
- Electromagnetic Interference: Other electronic devices or metal/liquid objects can sometimes interfere with RFID signals, impacting performance.
Video doorbell TA2021
Ship or pick up from our office.
Video doorbell TA2021
A video doorbell, also known as a smart doorbell or doorbell camera, is an upgraded version of a traditional doorbell that incorporates a built-in camera, microphone, and speaker. It's connected to your home's Wi-Fi network and allows you to see, hear, and speak to visitors at your front door from anywhere using a smartphone app or other connected devices. Here are the key features and how they work:- Built-in Camera: This is the core feature, providing a live video feed of your doorstep. Most video doorbells offer high-definition (HD) video, and many include features like night vision (infrared or color) for clear viewing in low light.
- Motion Detection: Video doorbells are equipped with sensors that detect movement in front of your door, even if someone doesn't ring the bell. When motion is detected, you'll receive an alert on your phone. Many advanced models use AI to differentiate between people, pets, packages, and vehicles, reducing false alarms.
- Two-Way Audio: A built-in microphone and speaker enable you to have a real-time conversation with whoever is at your door, whether you're home or away. This is useful for speaking with delivery drivers, guests, or even deterring unwanted visitors.
- Remote Access (via App): Through a dedicated smartphone app, you can view the live camera feed, receive notifications, and communicate with visitors from anywhere with an internet connection.
- Recording and Storage: Video doorbells typically record footage when motion is detected or the doorbell is pressed. This footage can be stored either locally (e.g., on an SD card within the device) or in the cloud (often requiring a subscription service).
- Connectivity: Most video doorbells connect to your home's Wi-Fi. They can be either hardwired to your existing doorbell wiring for continuous power or battery-powered for easier wireless installation.
- Smart Home Integration: Many video doorbells can integrate with other smart home systems and devices, such as smart speakers (like Amazon Alexa or Google Assistant) or smart locks, allowing for a more connected and automated home security experience.
- Enhanced Security: Provides real-time monitoring of your front door, allowing you to see and record who comes and goes, deterring potential intruders and package thieves.
- Convenience: Answer your door and communicate with visitors from anywhere, without having to physically be home or get up to open the door.
- Peace of Mind: Know who is at your door, even when you're not there, and receive alerts about any activity.
- Evidence Collection: Recorded footage can serve as valuable evidence in case of a security incident.