Access Control
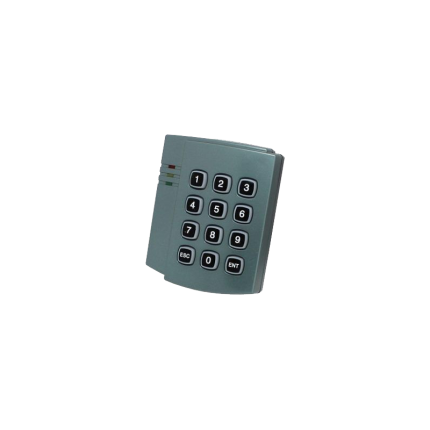
Keypad access control -Key Automation EGKTB1
PRODUCT SHEET PDF
While a specific image of the EGKTB1 is not available in the search results, the description aligns with the typical features and functionality of a keypad used for access control. You can likely find images of similar keypads by searching for "Keypad Access Control" or "Keypad Security System".
Keypad access control -Key Automation EGKTB1
*BUS decoder powered *Rain Shield Cover Included *Touch *Protection degree: IP 55 *BacklightTECHNICAL FEATURES
| Duty cycle percentage | % | 100% |
| Voltage | Vac | 10-24 |
| Voltage | Vdc | 12-34 |
| AC Voltage Frequency | Hz | 50/60 |
| Nominal power | W | 0,25 |
| Peak power | W | 1,5 |
| Appliance isolation class | III | |
| Degree of protection | IP | 55 |
| Dimensions (L - D - H) | mm | 79 - 23 - 79 |
| Item | kg | 0,25 |
| Minimum operating temperature | °C | -10 |
| Max operating temperature | °C | +55 |
The Keypad Key Automation EGKTB1 is a keypad used for access control.
It's a type of electronic keypad that likely integrates with a security system to allow entry based on a code or combination.
Keypads like the EGKTB1 typically replace traditional keys and locks, providing a more secure and convenient way to manage access to a building or specific areas within a building.
Here's a more detailed explanation:
-
Access Control:The primary function of the EGKTB1 is to control access to a secured area.
-
Keypad Functionality:It allows users to enter a pre-set code using the keypad's buttons. This code is then verified by the connected security system.
-
Integration:It's designed to connect with a security system or control unit, often using a Wiegand protocol, to manage access permissions.
-
Security:Keypads offer a more secure alternative to traditional keys because they can be reprogrammed with new codes, and they eliminate the need to physically distribute keys.
-
Convenience:Keypads offer a convenient way to manage access, especially in situations where there are many users or frequent changes in access needs.
Keypad access control K100SC104
Ship or pick up from our office.
Keypad access control K100SC104
(Recommended for indoor usage) *Rain Shield Cover is included *Waterproof Version *EM/ID card/tag reader *Backlight *500 User *DC 12 VKeypad Access Control K110V2000
Keypad Access Control K110V2000
*Waterproof Version *EM - RFID card/tag reader *Finger Touch *Backlight *DC 12 V *1000 Users *Doorbell button *Rain Shield Cover IncludedThe Keypad Access Control K110V2000 is a standalone access control system designed for single-door access, typically used for residential or small-to-medium commercial buildings.
It allows users to unlock the door using either a proximity card, a PIN code, or a combination of both.
Here's a more detailed breakdown:
Key Features:
- Multiple User Capacity: It can support up to 1000 users.
- Multiple Access Methods: Users can unlock the door using RFID cards, PIN codes, or both.
- Standalone Operation: It functions independently, without needing to be connected to a central computer.
- Wiegand Input/Output: It can connect to an external card reader (Wiegand 26 input) and a controller (Wiegand 26 output).
- Tamper Alarm: Includes a tamper alarm for added security.
- Backlit Keypad: The keypad is backlit, making it easier to use in low-light conditions.
- Short Circuit Protection: The output is automatically turned off if there's a short circuit in the electric lock or alarm output.
- Waterproof: Some models, like the V2000-C, are waterproof, making them suitable for outdoor use.
- Easy Installation and Programming: The system is designed for straightforward installation and programming.
- Doorbell Input: Some models include a doorbell input.
- Adjustable Settings: Features like door output time, alarm time, and door open time can be adjusted.
Applications:
- Residential Buildings: Ideal for controlling access to apartments or individual homes.
- Small to Medium Businesses: Suitable for offices, shops, and other commercial spaces.
- Warehouses and Factories: Can be used to manage access to secure areas.
- Other Applications: Laboratories, banks, and even prisons.
Keypad Access Control K155ST15
Ship or pick up from our office.
Keypad Access Control K155ST15
*Rain Shield Cover included *EM/ID card/tag reader *Finger Touch *Backlight *2000 Users *DC 12 V *IP 67 (Waterproof) *Doorbell button This unit is a standalone access controller or a Wiegand output keypad/card reader suitable for mounting indoors or outdoors, even in harsh environments. It features a sturdy, vandal proof Zinc Alloy electroplated case available in bright silver or matte silver finishes. The electronics are fully potted, ensuring durability. With support for up to 2000 users in Card, PIN, or Card + PIN configurations, this unit is ideal for small shops, domestic households, as well as commercial and industrial applications such as factories, warehouses, laboratories, banks, and prisons.Key Features
- Waterproof: IP68 rated for outdoor use
- Material: Strong Zinc Alloy Electroplated anti vandal case
- User Capacity: 2000 users, supports Card, PIN, Card + PIN
- Adjustable Timers: Door output time, Alarm time, Door Open time
- Short Circuit Protection: Lock output current short circuit protection
- Built in Features: Light dependent resistor (LDR) for anti tamper, built in buzzer
- LED Status Indicators: Red, Yellow, and Green LEDs display the working status
Technical Specifications
- Operating Voltage: DC 12V ±10%
- User Capacity: 2000
- Card Reading Distance: 3 6 cm
- Active Current: < 60mA
- Idle Current: 25 ± 5mA
- Lock Output Load: Max 3A
- Alarm Output Load: Max 20A
- Operating Temperature: 45 60
- Operating Humidity: 10% 90% RH
- Adjustable Door Relay Time: 0 99 seconds
- Adjustable Alarm Time: 0 3 minutes
- Wiegand Interface: Wiegand 26 bit
- Size: 120 x 76 x 23mm
- Wiring Connections: Electric Lock, Exit Button, External Alarm, External Reader
Keypad Access Control K170S300A
Keypad Access Control K170S300A
*Rain Shield Cover Included *Waterproof Version *EM/ID card/tag reader *Backlight *DC 12 V *Shock resistance *Anti-vandal Metal shell *Doorbell Button Wiegand Output: Equipped with a Wiegand output for seamless integration with a controller. Multiple Access Modes: Offers Card, PIN, or Card + PIN options, providing versatile access control methods. Durable Metal Case: Housed in a robust Zinc Alloy electroplated case, ensuring durability and vandal resistance. RFID Key Fob Duplicator Attribute-Based Access Control Vs Role-Based Access Control 1,000 User Capacity: Supports up to 1,000 users, ideal for large-scale access control in commercial and industrial settings. Backlight Keypad: Features a backlight keypad for easy operation in low-light conditions.Description
1000 Users Metal Case 125KHZ RFID Card Keypad Access Controller with Backlight Door Control Independent Code Access Device
Description
Single door multifunction standalone access controller or a Wiegand output keypad or card reader.
It is suitable for mounting either indoor or outdoor in harsh environments.
It is housed in a strong, sturdy and vandal proof Zinc Alloy electroplated case which is availabl in either a bright silver or matt silver finish.
Metal Case&Waterproof .Supports up to 1000 users in either a Card, 4 digit PIN, or a Card + PIN option.
The inbuilt card reader supports125KHZ EM cardsLock output current short circuit protection, Wiegand output , and a backlight keypad.
Ideal choice for door access not only for small shops and domestic households but als for commercial and industrial applications such as factories, warehouses, laboratories, banks and prisons.
Features
Simple Programming, Easy Operatio
Adopt function steady card reader of block
Keypad Locks for 30 Seconds After 10 False Entrie
Can be Connected with Door-open Button and Doorbel
Non-volatile Memory in Power Failure
Tamper Switch can be Connected to Security Alarm System
Backlight key
Wiegand 26 output for connection to a controller
Support 1000Users
Keypad Access Control K280S6
Keypad Access Control K280S6
*Rain Shield Cover included *Backlight *DC 12-24 V *EM/ID card/tag reader *2000 Users *Doorbell *Shock resistance *Anti-vandal Metal shell *IP67Keypad access control is a security system that uses a keypad to restrict entry to authorized individuals by requiring them to enter a specific code.
Instead of physical keys, users input a PIN or code on the keypad, and if the code is correct, the system unlocks the door or gate.
Here's a more detailed explanation:
How it works:
-
Keypad:A keypad, typically with numbered buttons, is installed at the entry point.
-
Code Entry:Users enter a pre-defined code on the keypad.
-
Access Granted:If the code matches the system's records, the door or gate is unlocked, granting access.
-
Security:Keypad access control systems offer a higher level of security than traditional locks and keys, as codes can be changed and managed more easily.
-
Convenience:They provide keyless entry, eliminating the need to carry physical keys or fobs.
-
Integration:Keypad systems can be integrated with other security systems, such as access control panels or alarm systems.
Types of Keypad Access Control:
-
Standalone:These systems are self-contained and don't require external software or computers.
-
Networked:These systems are connected to a network, allowing for centralized management and reporting.
-
Integrated:Keypads can be part of a larger access control system, often combined with other methods like RFID cards or biometrics.
Common Applications:
-
Residential Buildings:Keypads can be used for entry into apartment buildings, condos, or individual units.
-
Commercial Buildings:Keypads are used for access control in offices, retail stores, and other businesses.
-
Industrial Facilities:Keypads can control access to restricted areas in factories and warehouses.
-
Gates and Barriers:Keypads can be used to control access to parking lots, garages, or other gated areas.
Benefits of Keypad Access Control:
-
Enhanced Security:Keypads provide a secure way to manage access, reducing the risk of unauthorized entry.
-
Increased Convenience:Keyless entry eliminates the hassle of carrying keys.
-
Scalability:Keypad systems can be easily scaled to accommodate changes in access requirements.
-
Cost-Effectiveness:Keypad systems can be a cost-effective solution for access control, especially when compared to more complex systems.
Keypad KO05SC107
Ship or pick up from our office.
Keypad KO05SC107
*Waterproof Keypad Version *EM/ID card/tag reader *Backlight Keypad *1000 Users *DC 12 V *Rain Shield Cover included in the keypad packageRFID Card Access Control
Ship or pick up from our office.
RFID Card Access Control
RFID card access control is a system that uses Radio Frequency Identification (RFID) technology to manage and control access to physical spaces. It provides a secure and convenient way to grant or deny entry to authorized individuals, replacing traditional keys or swipe cards. This system works by wirelessly communicating between an RFID card (or tag) and an RFID reader. How it Works- RFID Card (Tag): Each authorized individual carries an RFID card, key fob, or even a smartphone with an embedded RFID chip. This chip contains a unique identification code and sometimes other encrypted data.
- RFID Reader: Readers are installed at entry points (doors, gates, elevators, etc.). They constantly emit a radio frequency field.
- Communication: When an RFID card enters the reader's field, the card's antenna captures energy from the reader's signal. This energizes the microchip on the card, allowing it to transmit its unique data back to the reader.
- Data Verification: The RFID reader decodes the information from the card and sends it to a central access control server or control panel. This server compares the card's data with a secure database of authorized users and their access permissions.
- Access Grant/Denial: If the credentials match an authorized profile, the system sends a signal to an electronic lock mechanism, allowing entry. If not, access is denied. This entire process typically happens in milliseconds.
- Audit Trail: The system also records detailed access information, including the time, date, and specific access point used, providing a valuable audit trail for security purposes.
- RFID Cards/Tags: These are the credentials held by users, typically in the form of plastic cards, key fobs, or even integrated into mobile devices. They contain a microchip and an antenna.
- RFID Readers (Interrogators): Devices installed at entry points that emit radio waves to communicate with the tags and read their data.
- Access Control Panel/Server: This is the "brain" of the system. It receives data from the readers, verifies user credentials against a database, and controls the electronic locks. It can be cloud-based or local.
- Electronic Locks: Devices that secure the entry points and are controlled by the access control system (e.g., magnetic locks, electric strikes).
- Access Control Software: Software used to manage user profiles, set access levels, monitor events, and generate reports.
- Passive RFID Tags: Most common for access control. They don't have an internal battery and are powered by the electromagnetic field emitted by the reader. They have a shorter read range (a few centimeters to a meter).
- Active RFID Tags: These tags have their own power source (battery), allowing for a much longer read range (up to several hundred meters) and the ability to broadcast signals periodically. They are typically more expensive.
- Semi-Passive RFID Tags: These tags have a battery to power the chip but only transmit data when activated by a reader's signal, offering improved sensitivity and performance over passive tags.
- Convenience: Offers contactless and keyless entry, making it fast and easy for users to gain access. Cards can often be read from inside a wallet or bag.
- Enhanced Security: Provides unique identification and can utilize encrypted communication, making tags difficult to duplicate. Lost cards can be immediately deactivated, preventing unauthorized use.
- Efficiency: Streamlines entry and exit processes, reducing wait times, especially in high-traffic areas.
- Flexibility & Scalability: Easily allows for adjusting access permissions for different users, areas, or time frames. Systems can be expanded or modified as needs change.
- Integration: Can be integrated with other security systems like CCTV, alarms, and time attendance systems for comprehensive security management.
- Audit Trails: Provides real-time tracking of who enters and exits, offering valuable data for security monitoring and incident investigation.
- Durability: RFID components generally experience less wear and tear compared to traditional mechanical locks or swipe card systems.
- Skimming: In theory, unauthorized readers could attempt to read card information if they get close enough, though modern RFID cards often use one-time codes and encryption to mitigate this risk.
- Cloning: If the security protocols are weak, an RFID card's information could potentially be cloned.
- Electromagnetic Interference: Other electronic devices or metal/liquid objects can sometimes interfere with RFID signals, impacting performance.
RFID Tag Access Control
Ship or pick up from our office.
RFID Tag Access Control
RFID Tag Access Control is a system that uses Radio Frequency Identification (RFID) technology to manage and control access to physical spaces or logical systems. It allows only authorized individuals or items to enter secure areas by wirelessly reading data stored on RFID tags. Think of it as a modern, electronic key system where your "key" is an RFID tag (like a card or key fob) and the "lock" is an RFID reader. How it Works ⚙️ The fundamental principle is straightforward:- RFID Tag/Credential: Each authorized individual or item is assigned an RFID tag. This tag contains a microchip that stores a unique identification code and an antenna.
- RFID Reader: A reader (also called an interrogator) is installed at the access point (e.g., a door, gate, or turnstile). The reader emits radio waves.
- Communication: When an RFID tag comes within range of the reader's radio waves, the tag's antenna captures energy from the reader's signal (for passive tags) or uses its own power source (for active tags) to activate its microchip. The tag then transmits its unique data back to the reader.
- Data Processing: The reader decodes the information from the tag and sends it to a central access control software or system.
- Authentication and Decision: The software compares the tag's unique ID with a database of authorized users and their assigned permissions. If the ID is valid and the user has permission to access that specific area at that time, the system sends a signal to unlock the door, open the gate, or grant access. If not, access is denied.
- Logging: The system typically logs every access attempt (both granted and denied), providing an audit trail for security monitoring and compliance.
- RFID Tag Access Controls/Credentials: These are the physical devices carried by users. They come in various forms, such as:
- Cards: Similar to credit cards, commonly used for employee badges or hotel key cards.
- Key Fobs: Small, convenient devices attached to keychains.
- Wristbands: Often used in recreational facilities or for events.
- Stickers/Labels: Can be affixed to items or vehicles.
- Mobile Credentials: Increasingly, smartphones can act as RFID tags through NFC (Near Field Communication), a subset of HF RFID.
- RFID Readers: Devices that emit radio waves to energize and read data from RFID tags. They can be fixed (at entry points) or mobile (handheld scanners).
- Antennas: Integral to the reader (or external), they transmit and receive radio signals to and from the tags. The antenna design influences the read range and reliability.
- Access Control Software/Management System: The "brain" of the system. This software manages user databases, assigns access permissions, logs events, and allows administrators to configure and monitor the system remotely.
- Access Control Panel/Controller: Hardware that connects the readers to the central software, processing data and controlling the locking mechanisms.
- Passive RFID Tags:
- Do not have an internal power source.
- They draw power from the radio waves emitted by the reader to operate.
- Are generally smaller, less expensive, and require no maintenance.
- Have a shorter read range (a few centimeters to a few feet).
- Most commonly used in access control for cards and key fobs.
- Active RFID Tags:
- Have their own internal power source (battery).
- Can transmit data over longer distances (up to several hundred meters) and at regular intervals.
- Are larger and more expensive.
- Often used for long-range applications like vehicle tracking or asset management.
- Semi-Passive RFID Tags (Battery-Assisted Passive - BAP):
- Contain a battery to power the microchip, but still rely on the reader's signal to initiate communication.
- Offer better read range and performance than passive tags, without continuously transmitting like active tags.
- Low Frequency (LF) RFID (125-134 kHz):
- Short read range (1-10 cm).
- Less susceptible to interference from metal and water.
- Common in traditional access control systems.
- High Frequency (HF) RFID (13.56 MHz):
- Moderate read range (10 cm-1 meter).
- Widely used for access control, ticketing, and Near Field Communication (NFC) applications (like smartphone taps).
- Ultra-High Frequency (UHF) RFID (300 MHz-3 GHz, often 860-960 MHz for RAIN RFID):
- Long read range (up to 12 meters).
- More susceptible to interference from liquids and metals.
- Used in applications requiring longer read distances, such as vehicle access control or large-scale inventory tracking.
Smart Video Doorbell
Ship or pick up from our office.
Smart Video Doorbell
*WiFi connection *Android/IOS app on the smartphone *Answer visitors using smartphone worldwideUHF Card
Ship or pick up from our office.
UHF Card
UHF (Ultra High Frequency) Card Access Control is a system that uses Ultra High Frequency Radio-Frequency Identification (UHF RFID) technology for managing and controlling access to various areas. Unlike traditional access control systems that require a close proximity tap or swipe, UHF systems leverage the longer read range of UHF RFID to provide hands-free, faster, and more efficient access. How it Works ⚙️ The core components of a UHF Card Access Control system are:- UHF Cards/Tags: These are typically cards, key fobs, or even vehicle tags embedded with a UHF RFID inlay. They contain a unique identification number or other encoded data.
- UHF Readers: These devices emit radio waves in the UHF frequency range (typically 860-960 MHz). When a UHF card/tag enters the reader's range, the tag is powered by the radio waves and transmits its unique data back to the reader.
- Antennas: Integrated within or connected to the readers, these are responsible for transmitting and receiving the radio signals.
- Access Control Software/System: This software receives the data from the reader, verifies the tag's credentials against a database, and then grants or denies access based on predefined rules. If access is granted, it sends a signal to unlock a door, open a gate, etc.
- Tag enters field: A person with a UHF card or a vehicle with a UHF tag approaches the reader.
- Reader transmits signal: The UHF reader continuously emits radio waves.
- Tag responds: The passive UHF tag, powered by the reader's signal, transmits its unique ID back.
- Data received and processed: The reader captures the tag's data and sends it to the access control system.
- Access granted/denied: The system verifies the credentials and, if authorized, activates the access point (e.g., opens a barrier). This entire process happens wirelessly and often within milliseconds.
- Long Read Range: Unlike Low Frequency (LF) and High Frequency (HF) RFID systems, UHF can read tags from several meters away (up to 10-15 meters or more depending on the setup). This allows for hands-free access, such as for vehicles entering a parking lot or individuals walking through a gate without stopping.
- High-Speed Data Transmission and Multiple Tag Reading: UHF readers can read many tags simultaneously and quickly (hundreds of tags per second). This is crucial for high-traffic areas, reducing bottlenecks and improving efficiency.
- Convenience and Efficiency: Users don't need to physically present or swipe a card, leading to a smoother and faster access experience. This is especially beneficial in applications like vehicle access, parking management, and large event entry.
- Enhanced Security: UHF tags are difficult to counterfeit, and the systems often incorporate encryption and password protection to prevent unauthorized access and data manipulation. Real-time tracking capabilities can also enhance security oversight.
- Scalability and Centralized Management: Cloud-based UHF access control platforms allow administrators to manage users, permissions, and access points remotely and in real-time, making it easy to scale for larger organizations or multiple locations.
- Durability and Cost-Effectiveness (Long Term): UHF components are generally robust and durable, leading to lower maintenance and replacement costs over time compared to traditional systems.
- Low Frequency (LF) RFID (125-134 kHz):
- Read Range: Very short (typically a few centimeters).
- Characteristics: Less susceptible to interference from metal and liquids.
- Common Uses: Animal identification, car immobilizers, older access control systems where close proximity is acceptable.
- High Frequency (HF) RFID (13.56 MHz):
- Read Range: Short (up to 1 meter).
- Characteristics: Good for secure data transfer and applications requiring closer interaction. Often used with Near Field Communication (NFC).
- Common Uses: Contactless payments (e.g., Apple Pay, Google Pay), smart cards for building access, public transport ticketing, library systems.
- Ultra High Frequency (UHF) RFID (860-960 MHz):
- Read Range: Long (several meters up to 15+ meters).
- Characteristics: Ideal for long-range, high-speed identification of multiple items. More susceptible to interference from metals and liquids than LF/HF, though specialized tags and antenna designs can mitigate this. The industry standard for passive UHF RFID is often referred to as RAIN RFID.
- Common Uses: Vehicle access control, inventory management, supply chain tracking, asset tracking, automated toll collection, large-scale personnel tracking.