Shop
Power inverter 110 V to 220 V
Ship or pick up from our office.
Power inverter 110 V to 220 V
A power inverter 110V to 220V (also known as a step-up voltage converter) is an electronic device that transforms an input voltage of 110 volts (V) into an output voltage of 220V. This type of inverter is crucial for bridging the gap between different regional electrical standards. How It Works At its core, a 110V to 220V power inverter utilizes a transformer to achieve the voltage conversion. Here's a simplified explanation:- Input (DC to AC Conversion for Inverters): While the prompt asks about a "power inverter 110V to 220V," it's important to clarify that traditional inverters convert DC (Direct Current) from a battery (e.g., 12V, 24V, 48V) into AC (Alternating Current). If the input is already 110V AC, then the device is more accurately called a voltage converter or transformer, as it's stepping up AC to AC. However, some inverters are designed to take a DC input and produce 110V AC or 220V AC, or even both.
- Step-Up Transformation: For a 110V AC to 220V AC conversion, the device contains a transformer with primary and secondary coils. The 110V AC from the power source is fed into the primary coil. Through electromagnetic induction, this voltage is "stepped up" to 220V in the secondary coil, which then becomes the output.
- Waveform: Inverters and converters can produce different types of AC waveforms:
- Pure Sine Wave: This is the most desirable waveform, replicating the smooth, consistent power from a utility grid. It's ideal for sensitive electronics.
- Modified Sine Wave: This is a cruder approximation of a sine wave and is generally suitable for less sensitive appliances, but can cause issues or damage with certain delicate electronics.
- Power Capacity (Wattage): This indicates how much power the device can supply. Ensure it's sufficient to handle the total wattage of the appliances you intend to connect. Exceeding the inverter's capacity can lead to damage.
- Efficiency: A higher efficiency rating means less energy is wasted as heat during the conversion process, which is important for battery-powered setups.
- Safety Features: Look for features like overload protection, short-circuit protection, and surge protection to safeguard your appliances and the inverter itself.
- Frequency: Electrical grids operate at either 50 Hz or 60 Hz. Ensure the inverter's output frequency matches the requirements of your appliances. Some inverters can switch between frequencies.
- Portability: Some are designed for travel, while others are larger for industrial or home use.
- International Travel: They allow travelers from countries with 110V systems (like North America) to use their 220V appliances (like hair dryers, chargers) in countries with 220V outlets (common in Europe, Asia, and other regions).
- Using Imported Appliances: If you have an appliance designed for 220V (e.g., a European kitchen appliance) but your home has 110V outlets, a step-up converter enables you to use it.
- Industrial and Specialized Applications: In industries, they can be used for automation and control systems, telecommunications, and emergency power systems to ensure compatible power supply for various equipment.
- Renewable Energy Systems: In off-grid solar or wind power setups, inverters convert DC power from batteries into the required AC voltage (which could be 110V or 220V depending on the load).
- High-Power Appliances: Some larger appliances or specialized tools might require 220V power, even in regions where 110V is standard for most household items. A converter can provide the necessary voltage without extensive electrical rewiring.
Safety sensor – BFT FL130
Ship or pick up from our office.
Safety sensor - BFT FL130
The BFT FL130 is a photoelectric safety sensor designed primarily for use with automated gates and doors. It's a crucial safety component that prevents the gate or door from closing if an obstacle, such as a person or vehicle, is detected in its path. Here's a breakdown of its key aspects: How it Works The BFT FL130 operates as a pair of photocells, consisting of a transmitter (TX) and a receiver (RX). These units are typically mounted on opposite sides of the gate or door opening. The transmitter emits an infrared beam towards the receiver. If anything breaks this beam (e.g., a person walking through, a car passing), the receiver detects the interruption and sends a signal to the gate's control unit. This signal then triggers a safety mechanism, causing the gate to stop its movement or reverse direction to avoid impact. Features and Specifications- Type: Photoelectric safety sensor (photocell).
- Components: Transmitter and receiver pair.
- Function: Detects obstacles in the path of automated gates and doors to prevent accidents.
- Detection Method: Infrared beam.
- Applications: Commonly used in residential and commercial settings for automated swing gates, sliding gates, and garage doors.
- Max Range: Up to 30 meters (can be reduced by 50% in adverse weather conditions like fog or heavy rain).
- Power Supply: Typically 20-31 VAC or 22-30 VDC.
- Absorption: Approximately 70mA per pair.
- Relay Contacts: 1A at 24 VAC-DC.
- Working Temperature: Generally from -15°C to +70°C (some sources say -5°C to +70°C).
- Protection Rating: IP54, meaning it's protected against dust ingress and splashing water.
- Mounting: Should be aligned and mounted at a height between 40 and 60 cm from the ground on flat, parallel surfaces.
- Dimensions: Compact, typically around 115mm x 32mm x 26mm.
- Versions: There is also a BFT FL130B version, which may offer additional features like self-alignment and is designed to meet EN12453 regulations for Type D safety devices when connected to a compatible control unit that verifies safety device functionality.
Pedestrian gate manual lock (One side key)
Ship or pick up from our office.
Pedestrian gate manual lock (One side key)
A "pedestrian gate manual lock (one side key)" refers to a type of locking mechanism for a gate that is operated manually and requires a key to unlock it from one side, while the other side allows for easy exit without a key. Here's a breakdown of its key features:- Manual Operation: This lock doesn't rely on electricity or automation. You physically use your hand to engage or disengage the locking mechanism.
- One-Sided Key Access: The defining characteristic is that a physical key is needed to unlock the gate from one specific side (usually the exterior or entry side).
- Easy Exit (Thumb-Turn, Latch, or Push Pad): On the interior or exit side, there's typically a simple mechanism like a thumb-turn, lever, push pad, or a basic latch that allows for quick and easy opening without needing a key. This is often a safety feature, especially for emergency exits.
- Security: It provides a basic level of security, preventing unauthorized entry from the keyed side.
- Power Independence: Since it's manual, it's not affected by power outages.
- Common Use Cases: These locks are frequently found on garden gates, backyard gates, pool gates, and other pedestrian access points where controlled entry is desired but a quick exit is also necessary.
Doorbell SDB111
Ship or pick up from our office.
Doorbell SDB111
The "Doorbell SDB111" primarily refers to a wired doorbell system that operates on a 12-volt DC power supply. It's often associated with Royal Electronics Technology Center Co. and is commonly used for security access control in homes, offices, and other buildings. Here's a breakdown of its typical characteristics about the doorbell SDB111:- Wired System: The "12V" in its name signifies that it's a wired doorbell, meaning it connects to a power source via electrical wires. This usually involves a transformer that converts household voltage to 12V DC.
- Low Voltage: Like many doorbell systems, it operates on low voltage for safety.
- Functionality: Its primary function is to produce a chime sound (like a "ding-dong") when the doorbell button is pressed. It's often chosen for its durability and continuous function without needing battery replacements.
- Installation: These doorbells can be installed with screws or double-sided adhesive tape and typically come with wiring diagrams.
- Security Integration: They are considered a good security measure as they are external and can be integrated with other security systems.
- Access Control: The SDB111 is specifically mentioned in the context of access control systems, suggesting its use in managing entry to a property.
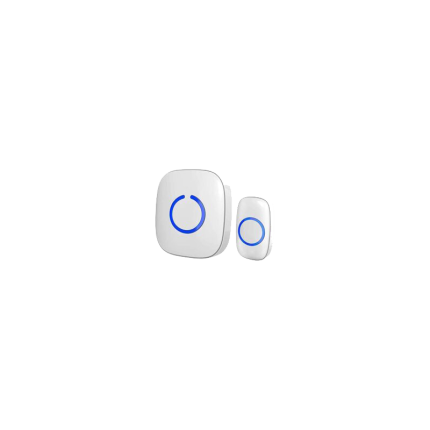
Wireless Doorbell
Ship or pick up from our office.
Wireless Doorbell
A wireless doorbell is a modern type of doorbell that operates without the need for physical wiring between the outdoor button and the indoor chime unit. Unlike traditional wired doorbells that rely on an electrical circuit, wireless doorbells use radio waves (or sometimes Wi-Fi or Bluetooth) to transmit a signal when the button is pressed. Here's a breakdown of its key components and how it works:- Transmitter (Doorbell Button): This is the part located outside your door that a visitor presses. It typically contains a small battery (though some "kinetic energy" versions generate power from the press itself) and sends a wireless signal when activated.
- Receiver (Chime Unit): This is the indoor component that produces the sound (chime or melody) when it receives the signal from the transmitter. Receivers can be battery-operated for portability or plug into a standard electrical outlet.
- When a visitor presses the doorbell button (transmitter), it sends a unique radio frequency (RF) signal.
- The signal travels wirelessly through the air.
- The receiver inside your home detects this signal.
- Upon receiving the signal, the receiver activates its chime or melody, alerting you to the visitor.
- Easy Installation: No need for complex wiring, drilling holes, or hiring an electrician. This makes them ideal for renters or anyone looking for a quick and simple setup.
- Flexibility and Portability: Since there are no wires, you can place the chime unit virtually anywhere in your home, and even move it around if needed. Many systems also allow for multiple receivers throughout a large house or property.
- Customization: Most wireless doorbells offer a variety of chime melodies and adjustable volume levels, allowing you to personalize the sound.
- Advanced Features (Smart Doorbells): Many modern wireless doorbells, often called "smart doorbells," integrate with Wi-Fi and offer additional features like:
- Video cameras: Allowing you to see who's at your door from your smartphone, even when you're not home.
- Two-way audio: Enabling you to speak with visitors remotely.
- Motion detection: Alerting you to activity outside your door.
- Smartphone notifications: Sending alerts to your phone when someone rings the bell or motion is detected.
- Integration with smart home systems: Connecting with other devices like smart lights or security systems.
- Enhanced Security: With features like video recording and remote monitoring, wireless doorbells can deter potential intruders and provide valuable evidence in case of an incident.
UHF Tag
Ship or pick up from our office.
UHF Tag
A UHF (Ultra-High Frequency) tag access control system is a security solution that uses radio frequency identification (RFID) technology operating in the ultra-high frequency range (typically 860-960 MHz) to control and monitor entry and exit of individuals or vehicles to restricted areas. 🛂 It's an automated system that identifies an individual or object with a unique RFID tag and, based on pre-defined permissions, grants or denies access. Unlike traditional barcode systems, UHF RFID doesn't require a direct line of sight between the tag and reader, allowing for longer read ranges and the ability to read multiple tags simultaneously. How It Works A UHF tag access control system generally consists of four main components:- UHF RFID Tags: These are small electronic devices containing a microchip and an antenna. The microchip stores data, such as a unique identifier or user information. Passive UHF tags, the most common type, are powered by the electromagnetic field emitted by the reader. Active tags have their own battery, enabling longer read ranges and continuous data transmission.
- UHF RFID Readers: These devices emit radio waves to create an electromagnetic field. When a UHF tag enters this field, it absorbs energy (for passive tags) and uses it to power its microchip. The tag then modulates the waves to transmit its stored data back to the reader. Readers can be fixed at entry points (like doors or gates) or handheld.
- Antennas: Integrated with the reader, antennas are responsible for transmitting and receiving the radio signals. Their design and placement are crucial for optimizing read performance and range.
- Access Control Software/Server: This is the "brain" of the system. The reader sends the decoded tag data to the software, which compares it against a database of authorized users and their assigned access levels. If the credentials match, the software sends a signal to unlock the door, open a gate, or trigger another access action. This software also logs all access events, providing an audit trail.
- Long Read Range: UHF systems can read tags from several meters away, making them ideal for applications like vehicle access control where you don't need to stop and present a card.
- High Read Speed and Multi-Tag Reading: They can quickly read multiple tags at once, which is beneficial in high-traffic areas or for tracking numerous assets simultaneously.
- Automation and Efficiency: Automated identification eliminates the need for manual checks, speeding up entry and exit processes.
- Enhanced Security: By identifying individuals and logging access events, these systems improve security and accountability. Features like encryption and unique IDs help prevent unauthorized access and cloning.
- Durability: UHF tags are often designed to be robust and can withstand various environmental conditions, making them suitable for outdoor or industrial use.
- Scalability: Systems can be easily expanded to cover more access points or accommodate a larger number of users.
- Vehicle Access Control: Automatically granting access to parking lots, gated communities, or corporate campuses without requiring drivers to stop and swipe a card.
- Building and Room Access: Controlling entry to offices, secure areas, or sensitive facilities for employees and authorized personnel.
- Event Management: Using RFID-enabled wristbands or badges for quick and efficient entry to concerts, theme parks, or VIP areas.
- Asset Tracking: While primarily for access, the same technology can track the movement of valuable assets within a controlled environment.
- Personnel Tracking: Monitoring the presence and movement of staff within a facility for safety or operational purposes.
- Interference: Performance can be affected by certain materials like metal and liquids in the environment, which can interfere with radio waves.
- Cost: Initial installation costs can be higher compared to simpler access control methods due to the specialized hardware and software.
- Regulatory Compliance: UHF frequencies are not globally harmonized, meaning system components must comply with regional radio regulations.
- Security Risks: While secure, like any digital system, there's a potential for sophisticated cloning or hacking attempts if not properly secured with encryption and robust protocols.
UHF Licence Plate
Ship or pick up from our office.
UHF Licence Plate
A UHF (Ultra High Frequency) Licence Plate access control system is a vehicle identification and access management solution that uses UHF RFID (Radio Frequency Identification) technology to automatically grant or deny entry to vehicles. Instead of relying on traditional license plate recognition (ANPR/LPR) which uses cameras to read visible plates, UHF systems use RFID tags, often in the form of stickers or cards, affixed to vehicles. 🚗 When a vehicle with a registered UHF RFID tag approaches an access point (like a gate or barrier), a UHF reader emits radio waves. The tag, powered by these waves, transmits its unique identification data back to the reader. This data is then sent to an access control system which verifies the vehicle's authorization. If authorized, the system triggers the gate to open, allowing for fast, hands-free, and seamless entry and exit. This technology is widely used in places requiring efficient and secure vehicle flow, such as:- Gated communities 🏡
- Parking facilities (corporate, commercial, residential) 🅿️
- Industrial sites and logistics hubs 🏭
- Toll roads 🛣️
- UHF RFID Tags: These are small, passive (battery-less) or semi-active devices that contain a microchip storing a unique identification number and an antenna. They are typically affixed to the vehicle's windshield or license plate. When exposed to radio waves from a reader, the tag's antenna collects energy, powering the microchip to transmit its data.
- UHF RFID Readers: These devices are installed at access points (e.g., gate entrances) and emit radio waves to detect and read the RFID tags on approaching vehicles. They have antennas to send and receive signals, and a processor to decode the data from the tags. UHF readers typically have a longer read range (up to 10-12 meters or more) compared to other RFID frequencies, allowing vehicles to pass without fully stopping.
- Access Control System (Software/Controller): This is the "brain" of the system. The reader sends the tag's ID number to this system. The access control software then compares this ID with its database of authorized vehicles. Based on pre-defined criteria (e.g., specific times of day, authorized user groups), it determines whether to grant or deny access.
- Barrier/Gate System: If access is granted by the control system, a signal is sent to the physical barrier (like a boom gate or sliding gate), which opens to allow the vehicle to pass.
- Speed and Efficiency 🚀: Vehicles don't need to stop or roll down windows, significantly reducing traffic congestion, especially during peak hours. This provides a "frictionless" entry experience.
- Long Read Range 📏: UHF RFID allows for detection from several meters away, enabling quick processing of vehicles even at higher speeds.
- Reliability in Diverse Conditions 🌧️☀️: Unlike optical ANPR systems that can be affected by dirt, rain, snow, or poor lighting, UHF RFID tags are generally more robust and less susceptible to environmental factors.
- Enhanced Security 🔒: RFID tags are difficult to duplicate or tamper with, offering a higher level of security than some other methods. The system also logs all entries and exits, providing a clear audit trail.
- Reduced Operational Costs 💰: Automation minimizes the need for manual gate attendants, leading to lower labor costs over time. There's also no need for physical cards or key fobs that can be lost or damaged, saving on replacement costs.
- Integration Capabilities 🔗: These systems can often integrate seamlessly with other security and management platforms, such as visitor management systems, surveillance cameras, and parking management software, for a comprehensive solution.
UHF Label
Ship or pick up from our office.
UHF Label
A UHF (Ultra-High Frequency) label access control system uses radio-frequency identification (RFID) technology operating in the ultra-high frequency range (typically 860-960 MHz) to manage and control access to specific areas, buildings, or resources. It's a touchless, automated system that offers long-range reading capabilities and the ability to identify multiple items simultaneously, making it highly efficient for various applications like vehicle access, personnel tracking in large facilities, and event management. 🛂 How it Works The core principle of a UHF label access control system relies on the communication between RFID tags (labels) and RFID readers. Here's a breakdown of the process:- RFID Tags (Labels): These are small electronic devices, often in the form of adhesive labels, cards, or embedded devices. They contain a microchip that stores unique identification data and an antenna. Most UHF tags used in access control are passive, meaning they don't have their own power source and rely on the energy emitted by the reader.
- RFID Reader: The reader emits radio waves, creating an electromagnetic field. When a UHF RFID tag enters this field, it absorbs energy from the waves, which powers its microchip.
- Data Transmission: Once activated, the tag modulates the waves to transmit its stored data (its unique ID) back to the reader.
- Data Processing and Verification: The reader captures and decodes this data, then sends it to a central access control system (often a computer with specialized software and a backend database). The system verifies the tag's unique ID against a list of authorized credentials and pre-defined access rules.
- Access Granting/Denial: If the tag is authorized, the system sends a signal to unlock a door, open a gate, or grant access. If not authorized, access is denied, and the system may trigger an alarm or log the attempted entry.
- Logging: The system typically records all entry and exit events, providing a detailed audit trail for security and management purposes.
- UHF RFID Tags/Labels: These are the physical identifiers worn by individuals or attached to vehicles/assets. They store the unique ID and are read by the system.
- UHF RFID Readers: These devices emit radio waves to power and read the data from the tags. They are strategically installed at entry/exit points (e.g., doorways, gates). Fixed readers are common for specific zones, while handheld readers offer flexibility for mobile applications like inventory or searching for tags.
- Antennas: Connected to the readers, antennas are responsible for transmitting and receiving the radio signals. The type and placement of antennas affect the read range and coverage area.
- Access Control Software/System: This is the "brain" of the system. It manages the database of authorized tags, processes the data received from readers, applies access rules, and controls the locking mechanisms. It often integrates with other security or building management systems.
- Backend Database: Stores all the information related to RFID tags, authorized users, access levels, and event logs.
- Locking Mechanisms: These are the physical devices controlled by the system, such as electronic door locks, gate barriers, or turnstiles.
- Long Read Range 📏: UHF systems can read tags from several meters away (typically 3-10 meters, and sometimes up to 25 meters or more), allowing for hands-free and rapid access, particularly useful for vehicles or large volumes of people.
- High-Speed Data Transmission and Multi-Tag Reading ⚡: They can read multiple tags simultaneously (often over 100 tags per second), significantly improving efficiency in high-traffic areas and during events.
- Enhanced Efficiency ⏱️: Automation of access eliminates manual checks, reduces queuing times, and frees up staff for other tasks.
- Improved Security 🔒: Each tag has a unique identifier, making it difficult to forge or duplicate. The system provides real-time monitoring and detailed audit trails, enhancing accountability and security. Integration with other systems like surveillance cameras can further bolster security.
- Touchless Operation 🖐️: The long read range enables touchless access, which is beneficial for hygiene, particularly in high-traffic areas or environments where physical contact should be minimized.
- Scalability 📈: UHF RFID systems can be easily scaled to accommodate a growing number of users and access points without compromising performance.
- Durability and Resistance 💪: UHF tags are often resistant to environmental factors like water, oil, and chemicals, and the data stored on their chips is protected. They can also be reused.
- Reduced Wear and Tear: As there's no physical contact with readers, the system components experience less wear and tear, leading to lower maintenance costs.
UHF Card
Ship or pick up from our office.
UHF Card
UHF (Ultra High Frequency) Card Access Control is a system that uses Ultra High Frequency Radio-Frequency Identification (UHF RFID) technology for managing and controlling access to various areas. Unlike traditional access control systems that require a close proximity tap or swipe, UHF systems leverage the longer read range of UHF RFID to provide hands-free, faster, and more efficient access. How it Works ⚙️ The core components of a UHF Card Access Control system are:- UHF Cards/Tags: These are typically cards, key fobs, or even vehicle tags embedded with a UHF RFID inlay. They contain a unique identification number or other encoded data.
- UHF Readers: These devices emit radio waves in the UHF frequency range (typically 860-960 MHz). When a UHF card/tag enters the reader's range, the tag is powered by the radio waves and transmits its unique data back to the reader.
- Antennas: Integrated within or connected to the readers, these are responsible for transmitting and receiving the radio signals.
- Access Control Software/System: This software receives the data from the reader, verifies the tag's credentials against a database, and then grants or denies access based on predefined rules. If access is granted, it sends a signal to unlock a door, open a gate, etc.
- Tag enters field: A person with a UHF card or a vehicle with a UHF tag approaches the reader.
- Reader transmits signal: The UHF reader continuously emits radio waves.
- Tag responds: The passive UHF tag, powered by the reader's signal, transmits its unique ID back.
- Data received and processed: The reader captures the tag's data and sends it to the access control system.
- Access granted/denied: The system verifies the credentials and, if authorized, activates the access point (e.g., opens a barrier). This entire process happens wirelessly and often within milliseconds.
- Long Read Range: Unlike Low Frequency (LF) and High Frequency (HF) RFID systems, UHF can read tags from several meters away (up to 10-15 meters or more depending on the setup). This allows for hands-free access, such as for vehicles entering a parking lot or individuals walking through a gate without stopping.
- High-Speed Data Transmission and Multiple Tag Reading: UHF readers can read many tags simultaneously and quickly (hundreds of tags per second). This is crucial for high-traffic areas, reducing bottlenecks and improving efficiency.
- Convenience and Efficiency: Users don't need to physically present or swipe a card, leading to a smoother and faster access experience. This is especially beneficial in applications like vehicle access, parking management, and large event entry.
- Enhanced Security: UHF tags are difficult to counterfeit, and the systems often incorporate encryption and password protection to prevent unauthorized access and data manipulation. Real-time tracking capabilities can also enhance security oversight.
- Scalability and Centralized Management: Cloud-based UHF access control platforms allow administrators to manage users, permissions, and access points remotely and in real-time, making it easy to scale for larger organizations or multiple locations.
- Durability and Cost-Effectiveness (Long Term): UHF components are generally robust and durable, leading to lower maintenance and replacement costs over time compared to traditional systems.
- Low Frequency (LF) RFID (125-134 kHz):
- Read Range: Very short (typically a few centimeters).
- Characteristics: Less susceptible to interference from metal and liquids.
- Common Uses: Animal identification, car immobilizers, older access control systems where close proximity is acceptable.
- High Frequency (HF) RFID (13.56 MHz):
- Read Range: Short (up to 1 meter).
- Characteristics: Good for secure data transfer and applications requiring closer interaction. Often used with Near Field Communication (NFC).
- Common Uses: Contactless payments (e.g., Apple Pay, Google Pay), smart cards for building access, public transport ticketing, library systems.
- Ultra High Frequency (UHF) RFID (860-960 MHz):
- Read Range: Long (several meters up to 15+ meters).
- Characteristics: Ideal for long-range, high-speed identification of multiple items. More susceptible to interference from metals and liquids than LF/HF, though specialized tags and antenna designs can mitigate this. The industry standard for passive UHF RFID is often referred to as RAIN RFID.
- Common Uses: Vehicle access control, inventory management, supply chain tracking, asset tracking, automated toll collection, large-scale personnel tracking.
UHF Gate Controller
Ship or pick up from our office.
UHF Gate Controller
A UHF Gate Controller is a system that uses Ultra-High Frequency (UHF) Radio Frequency Identification (RFID) technology to manage and control access through a gate or designated entry/exit point. It typically consists of a UHF RFID reader, antennas, and a control unit that processes the data and triggers the gate mechanism. It's designed for automated, hands-free identification and tracking of people or objects equipped with UHF RFID tags, offering a longer read range and faster processing compared to other RFID frequencies. How it Works The fundamental principle of a UHF Gate Controller relies on the interaction between a UHF RFID reader and UHF RFID tags. Here's a breakdown:- UHF RFID Reader and Antennas: The gate controller incorporates a UHF RFID reader connected to one or more antennas. These antennas emit radio waves in the UHF frequency band (typically 860-960 MHz).
- RFID Tags: People, vehicles, or items needing access are equipped with UHF RFID tags. These tags contain a microchip that stores data (like a unique ID) and an antenna. Passive UHF tags, which are common in these systems, do not have their own power source; they draw power from the radio waves emitted by the reader.
- Data Exchange: When a tagged item or person enters the read range of the gate's antennas, the RFID tag is energized by the reader's radio waves. The tag then modulates these waves to send its stored data back to the reader.
- Data Processing and Control: The UHF RFID reader receives the tag's data and sends it to a control unit (often an integrated part of the gate system or a separate access controller). This control unit verifies the tag's information against a database of authorized entries.
- Gate Activation: If the tag is authorized, the control unit sends a signal to open or enable the gate (e.g., a barrier arm, turnstile, or door lock). If the tag is unauthorized, access is denied, and an alarm might be triggered.
- Directional Detection and Anti-Collision: Advanced UHF gate controllers can detect the direction of movement (e.g., entering or exiting) and employ anti-collision algorithms to read multiple tags simultaneously, even in high-traffic scenarios. Some systems use additional sensors (like infrared) to improve accuracy and prevent "tailgating."
- Long Read Range: Typically able to read tags from several meters away, allowing for "hands-free" and "drive-through" access.
- High Reading Speed: Can quickly identify multiple tags in motion, reducing bottlenecks.
- Anti-Collision: Algorithms that allow the reader to differentiate and read multiple tags present in the field at the same time.
- Directional Sensing: Ability to determine if an item or person is entering or exiting the controlled area.
- Integration Capabilities: Often connect with other security or management systems via interfaces like Ethernet, RS232, RS485, or Wi-Fi.
- Robust Design: Many are built for industrial or outdoor environments, with resistance to dust and water.
- Vehicle Access Control: Managing entry and exit for parking lots, gated communities, corporate campuses, and toll roads. Vehicles can have tags on windshields, allowing for seamless, hands-free access.
- People Access Control: Controlling access to buildings, restricted areas, and for time and attendance tracking in offices, universities, hospitals, and event venues.
- Logistics and Warehouse Management: Monitoring the flow of goods, pallets, and containers in and out of warehouses, distribution centers, and production lines for inventory management, asset tracking, and theft prevention.
- Retail: Used at store exits for Electronic Article Surveillance (EAS) to prevent shoplifting, and for inventory tracking as items move in and out of the backroom.
- Libraries and Document Management: Tracking books, documents, and other assets as they enter or leave a facility.
- Manufacturing: Monitoring materials and finished products on production lines and at factory entrances/exits.
GSM Gate Controller RTU5024
Ship or pick up from our office.
GSM Gate Controller RTU5024
The GSM Gate Controller RTU5024 is a device that allows you to control gates, doors, and other electrical equipment remotely using a mobile phone. It functions as a GSM relay switch, meaning it utilizes the Global System for Mobile Communications (GSM) network to receive commands and activate a built-in relay. How it Works ⚙️ The RTU5024 operates by accepting calls from authorized phone numbers. When an authorized user dials the SIM card number installed in the RTU5024, the device recognizes the caller ID, rejects the call (so there are no call charges), and then activates its relay. This relay can be connected to the mechanism of a gate, door, or other machinery, effectively opening, closing, or switching it on/off. Users can also manage the device and its authorized numbers via SMS commands or a dedicated smartphone app. Key Features ✨- No Call Charges: The device rejects calls from authorized numbers after the first ring, meaning there are no charges incurred for operating it via phone call.
- Caller ID Authentication: It uses caller ID for identification, ensuring only authorized numbers can control the device. Unknown callers are ignored.
- Remote Operation: Can be operated from anywhere with GSM network coverage, with no distance limitations.
- User Management: Authorized phone numbers (typically up to 200, though some versions support more) can be added or removed via SMS text commands or through a smartphone app.
- Relay Output: Features one output with a relay rating (e.g., 3A/240VAC) for connecting to various switches or machines.
- SMS Confirmation: The device can be configured to send an SMS confirmation to the owner or authorized number after a relay action.
- Programmable Relay Time: The duration for which the relay remains open or closed is often programmable.
- Quad-band GSM: Works on universal GSM frequencies (850/900/1800/1900MHz), making it compatible with most GSM networks worldwide. Some versions also support 3G or 4G.
- Smartphone App: Available with companion apps for Android and iOS for easier configuration and control.
- No Physical Remote Needed: Eliminates the need for multiple physical remote controls or keys for different users.
- Access Control: Remotely opening/closing swing/sliding gates, garage doors, shutters, and pedestrian doors for residential, commercial, or industrial properties.
- Car Parking Systems: Controlling barriers and access for parking lots.
- Remote Equipment Control: Switching on/off various remote equipment like street lights, motors, pumps, fans, inverters, PLCs, and air conditioners.
- Agriculture: Remote control of agricultural pumps and irrigation systems.
- Business: Managing electronic boxes, billboards, and LED signs remotely.
- Security: Can be integrated into basic security systems for remote monitoring or activation of alarms.