gates
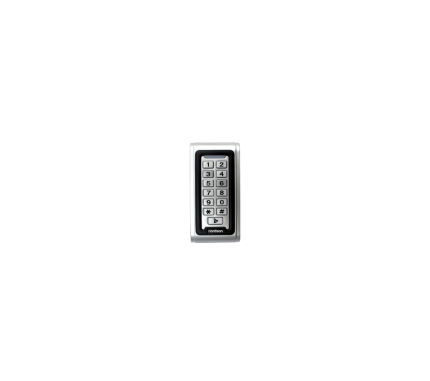
Keypad Access Control K155ST15
Ship or pick up from our office.
Keypad Access Control K155ST15
*Rain Shield Cover included *EM/ID card/tag reader *Finger Touch *Backlight *2000 Users *DC 12 V *IP 67 (Waterproof) *Doorbell button This unit is a standalone access controller or a Wiegand output keypad/card reader suitable for mounting indoors or outdoors, even in harsh environments. It features a sturdy, vandal proof Zinc Alloy electroplated case available in bright silver or matte silver finishes. The electronics are fully potted, ensuring durability. With support for up to 2000 users in Card, PIN, or Card + PIN configurations, this unit is ideal for small shops, domestic households, as well as commercial and industrial applications such as factories, warehouses, laboratories, banks, and prisons.Key Features
- Waterproof: IP68 rated for outdoor use
- Material: Strong Zinc Alloy Electroplated anti vandal case
- User Capacity: 2000 users, supports Card, PIN, Card + PIN
- Adjustable Timers: Door output time, Alarm time, Door Open time
- Short Circuit Protection: Lock output current short circuit protection
- Built in Features: Light dependent resistor (LDR) for anti tamper, built in buzzer
- LED Status Indicators: Red, Yellow, and Green LEDs display the working status
Technical Specifications
- Operating Voltage: DC 12V ±10%
- User Capacity: 2000
- Card Reading Distance: 3 6 cm
- Active Current: < 60mA
- Idle Current: 25 ± 5mA
- Lock Output Load: Max 3A
- Alarm Output Load: Max 20A
- Operating Temperature: 45 60
- Operating Humidity: 10% 90% RH
- Adjustable Door Relay Time: 0 99 seconds
- Adjustable Alarm Time: 0 3 minutes
- Wiegand Interface: Wiegand 26 bit
- Size: 120 x 76 x 23mm
- Wiring Connections: Electric Lock, Exit Button, External Alarm, External Reader
Keypad Access Control K280S6
Keypad Access Control K280S6
*Rain Shield Cover included *Backlight *DC 12-24 V *EM/ID card/tag reader *2000 Users *Doorbell *Shock resistance *Anti-vandal Metal shell *IP67Keypad access control is a security system that uses a keypad to restrict entry to authorized individuals by requiring them to enter a specific code.
Instead of physical keys, users input a PIN or code on the keypad, and if the code is correct, the system unlocks the door or gate.
Here's a more detailed explanation:
How it works:
-
Keypad:A keypad, typically with numbered buttons, is installed at the entry point.
-
Code Entry:Users enter a pre-defined code on the keypad.
-
Access Granted:If the code matches the system's records, the door or gate is unlocked, granting access.
-
Security:Keypad access control systems offer a higher level of security than traditional locks and keys, as codes can be changed and managed more easily.
-
Convenience:They provide keyless entry, eliminating the need to carry physical keys or fobs.
-
Integration:Keypad systems can be integrated with other security systems, such as access control panels or alarm systems.
Types of Keypad Access Control:
-
Standalone:These systems are self-contained and don't require external software or computers.
-
Networked:These systems are connected to a network, allowing for centralized management and reporting.
-
Integrated:Keypads can be part of a larger access control system, often combined with other methods like RFID cards or biometrics.
Common Applications:
-
Residential Buildings:Keypads can be used for entry into apartment buildings, condos, or individual units.
-
Commercial Buildings:Keypads are used for access control in offices, retail stores, and other businesses.
-
Industrial Facilities:Keypads can control access to restricted areas in factories and warehouses.
-
Gates and Barriers:Keypads can be used to control access to parking lots, garages, or other gated areas.
Benefits of Keypad Access Control:
-
Enhanced Security:Keypads provide a secure way to manage access, reducing the risk of unauthorized entry.
-
Increased Convenience:Keyless entry eliminates the hassle of carrying keys.
-
Scalability:Keypad systems can be easily scaled to accommodate changes in access requirements.
-
Cost-Effectiveness:Keypad systems can be a cost-effective solution for access control, especially when compared to more complex systems.
Keypad KO05SC107
Ship or pick up from our office.
Keypad KO05SC107
*Waterproof Keypad Version *EM/ID card/tag reader *Backlight Keypad *1000 Users *DC 12 V *Rain Shield Cover included in the keypad packageMercury Level Switch
Ship or pick up from our office.
Mercury Level Switch
A mercury level switch is a type of electrical switch that uses a small amount of liquid mercury to open or close an electrical circuit based on its position or the level of a liquid. Essentially, the mercury acts as a conductive bridge between electrical contacts. How it Works The core component of a mercury level switch is a sealed glass or metal capsule containing one or more electrical contacts and a small, free-moving drop of mercury. When the switch or the liquid it's monitoring changes its tilt or level:- Tilt Switches: Gravity pulls the mercury to the lowest point within the capsule. If the tilt is sufficient, the mercury will flow to connect two or more contacts, completing an electrical circuit. Tilting it in the opposite direction moves the mercury away, breaking the circuit.
- Float Switches: In liquid level applications, the mercury switch is often integrated with a float mechanism. As the liquid level rises or falls, the float moves, which in turn tilts the mercury switch, causing the mercury to connect or disconnect the contacts.
- Displacement Switches: Some designs use a "plunger" that dips into a pool of mercury, raising the mercury level to contact an electrode and complete the circuit.
- Thermostats: In older thermostats, they controlled heating and cooling systems.
- Sump Pumps: Used to automatically turn on the pump when water levels rise.
- Appliances: Found in washing machines (for lid switches and load balancing), chest freezers (for lid lights), and some gas appliances like ovens and water heaters (as flame sensors).
- Automotive Industry: Previously used for trunk lid lights, ride control, and anti-lock braking systems.
- Industrial Settings: Utilized in liquid level control and safety systems.
- Roll Sensing/Tip-over Warnings: For construction equipment or other vehicles operating on uneven terrain.
- Durability and Reliability: The sealed contacts prevent oxidation, leading to a long lifespan.
- Quiet Operation: No abrupt snapping of contacts.
- No Contact Erosion: Mercury's liquid nature prevents the wear and tear seen in mechanical contacts.
- Spark-Free: They don't produce sparks when making or breaking circuits, making them suitable for hazardous environments.
- Toxicity of Mercury: This is the primary and most significant disadvantage. Mercury is a highly toxic substance, posing serious environmental and health risks if released.
- Environmental Concerns: Improper disposal of mercury switches can lead to widespread contamination. Due to these concerns, the use of mercury switches has been largely phased out in many applications, especially in new products.
- Sensitivity to Gravity/Orientation: While an advantage for tilt sensing, it makes them unsuitable for portable or mobile devices where orientation changes or vibrations could cause false readings.
- Limited Functionality: Most mercury switches provide only a simple on/off function.
Micro Limit Switch
Ship or pick up from our office.
Micro Limit Switch
A micro limit switch, often simply called a micro switch, is a type of electrical switch that's characterized by its small size and the precise, rapid action it takes when a minimal amount of force is applied to its actuator. It's designed to detect the presence or position of an object or the end of a mechanical movement. These switches are known for their:- High sensitivity: They require very little force to activate.
- Rapid response: The internal contacts "snap" open or closed very quickly, regardless of how slowly the actuator is pressed. This snap-action mechanism helps to reduce arcing and extends the switch's lifespan.
- Reliability: They are built to withstand millions of operations, making them durable for long-term use.
- Compact size: Their small footprint allows them to be used in applications where space is limited.
- Actuator: This is the external part that an object or mechanical component presses against. It can be a button, a lever (with or without a roller), a plunger, or other forms.
- Internal spring mechanism: This provides the "snap-action." When the actuator is pressed to a certain point (the "trip point"), the spring mechanism rapidly moves the contacts.
- Contacts: These are the electrical components that open or close the circuit. Micro switches usually have three terminals:
- Common (C): The input terminal.
- Normally Open (NO): This contact is open (no current flows) when the switch is unactivated and closes when the switch is actuated.
- Normally Closed (NC): This contact is closed (current flows) when the switch is unactivated and opens when the switch is actuated
- Household Appliances:
- Microwave ovens: To detect if the door is closed before operating.
- Washing machines: For door interlocks and water level detection.
- Refrigerators: To turn the light on/off when the door opens/closes.
- Printers: To detect paper jams or the position of paper.
- Automotive Industry:
- Car doors: To detect if a door is open or closed (e.g., for interior lights or security systems).
- Brake pedals: To activate brake lights.
- Seat belt mechanisms: To detect if a seat belt is fastened.
- Industrial Automation:
- Conveyor systems: To detect the presence of items or the end of travel for a belt.
- Robotic arms: For precise positioning and limit detection of movement.
- Machine safety guards: To ensure guards are correctly positioned before machinery operates.
- Elevators and hoists: To prevent over-travel and ensure proper door operation.
- Consumer Electronics:
- Computer mice and keyboards: For button clicks.
- Vending machines: For coin detection or jam detection.
- Medical Equipment:
- In various diagnostic tools and surgical instruments for precise control.
- Pin Plunger: A simple button-like plunger that is directly pressed.
- Roller Lever: Features a lever with a roller at the end, ideal for applications with sliding or rotating components.
- Hinge Lever: A simple lever arm that pivots to actuate the switch.
- Flexible Roller: Similar to a roller lever, but with a more flexible arm to accommodate irregular surfaces or wider ranges of motion.
- Spring Plunger: A plunger supported by a spring, allowing for a certain degree of "overtravel" beyond the actuation point without damaging the switch.
Programmer module -Key Automation KUBEPRO
Ship or pick up from our office.
PRODUCT SHEET PDFProgrammer module -Key Automation KUBEPRO
*KUBEPRO - Installer Version *Smartphone programming for 14A and HALO control boardsThe Key Automation KUBEPRO is a programmer module that allows professional installers to configure and manage Key Automation gate and door operators using a smartphone.
It connects via Bluetooth to the installer's smartphone and allows them to adjust parameters, set up the gate opener, and manage other aspects of the automation system.
The KUBE PRO also includes the KEY CLOUD service for data viewing, backup, team management, and maintenance scheduling.
Here's a more detailed breakdown:
-
Purpose:The KUBEPRO is designed for professional installers to configure and manage Key Automation gate and door operators.
-
Functionality:It allows installers to adjust various parameters, set up the gate opener, and manage other settings directly from their smartphone.
-
Connectivity:It connects to the gate operator's control board and uses Bluetooth to communicate with the installer's smartphone.
-
Smartphone App:An app, specifically designed for professional installers, is used to interact with the KUBEPRO module.
-
KEY CLOUD:The KUBE PRO module includes KEY CLOUD, a cloud-based service for storing data, managing teams, and scheduling maintenance.
-
Accessibility:The KUBE PRO module is restricted to users with a Key Automation account, ensuring proper authorization and usage.
RFID Card Access Control
Ship or pick up from our office.
RFID Card Access Control
RFID card access control is a system that uses Radio Frequency Identification (RFID) technology to manage and control access to physical spaces. It provides a secure and convenient way to grant or deny entry to authorized individuals, replacing traditional keys or swipe cards. This system works by wirelessly communicating between an RFID card (or tag) and an RFID reader. How it Works- RFID Card (Tag): Each authorized individual carries an RFID card, key fob, or even a smartphone with an embedded RFID chip. This chip contains a unique identification code and sometimes other encrypted data.
- RFID Reader: Readers are installed at entry points (doors, gates, elevators, etc.). They constantly emit a radio frequency field.
- Communication: When an RFID card enters the reader's field, the card's antenna captures energy from the reader's signal. This energizes the microchip on the card, allowing it to transmit its unique data back to the reader.
- Data Verification: The RFID reader decodes the information from the card and sends it to a central access control server or control panel. This server compares the card's data with a secure database of authorized users and their access permissions.
- Access Grant/Denial: If the credentials match an authorized profile, the system sends a signal to an electronic lock mechanism, allowing entry. If not, access is denied. This entire process typically happens in milliseconds.
- Audit Trail: The system also records detailed access information, including the time, date, and specific access point used, providing a valuable audit trail for security purposes.
- RFID Cards/Tags: These are the credentials held by users, typically in the form of plastic cards, key fobs, or even integrated into mobile devices. They contain a microchip and an antenna.
- RFID Readers (Interrogators): Devices installed at entry points that emit radio waves to communicate with the tags and read their data.
- Access Control Panel/Server: This is the "brain" of the system. It receives data from the readers, verifies user credentials against a database, and controls the electronic locks. It can be cloud-based or local.
- Electronic Locks: Devices that secure the entry points and are controlled by the access control system (e.g., magnetic locks, electric strikes).
- Access Control Software: Software used to manage user profiles, set access levels, monitor events, and generate reports.
- Passive RFID Tags: Most common for access control. They don't have an internal battery and are powered by the electromagnetic field emitted by the reader. They have a shorter read range (a few centimeters to a meter).
- Active RFID Tags: These tags have their own power source (battery), allowing for a much longer read range (up to several hundred meters) and the ability to broadcast signals periodically. They are typically more expensive.
- Semi-Passive RFID Tags: These tags have a battery to power the chip but only transmit data when activated by a reader's signal, offering improved sensitivity and performance over passive tags.
- Convenience: Offers contactless and keyless entry, making it fast and easy for users to gain access. Cards can often be read from inside a wallet or bag.
- Enhanced Security: Provides unique identification and can utilize encrypted communication, making tags difficult to duplicate. Lost cards can be immediately deactivated, preventing unauthorized use.
- Efficiency: Streamlines entry and exit processes, reducing wait times, especially in high-traffic areas.
- Flexibility & Scalability: Easily allows for adjusting access permissions for different users, areas, or time frames. Systems can be expanded or modified as needs change.
- Integration: Can be integrated with other security systems like CCTV, alarms, and time attendance systems for comprehensive security management.
- Audit Trails: Provides real-time tracking of who enters and exits, offering valuable data for security monitoring and incident investigation.
- Durability: RFID components generally experience less wear and tear compared to traditional mechanical locks or swipe card systems.
- Skimming: In theory, unauthorized readers could attempt to read card information if they get close enough, though modern RFID cards often use one-time codes and encryption to mitigate this risk.
- Cloning: If the security protocols are weak, an RFID card's information could potentially be cloned.
- Electromagnetic Interference: Other electronic devices or metal/liquid objects can sometimes interfere with RFID signals, impacting performance.
Safety Sensor P52000H
Ship or pick up from our office.
Safety Sensor P52000H
IP Rating: IP54
Certification: CE
Working Voltage: 12V-24V AC/DC
Temperature Rane: -20ºC to 60 ºC
Protection Index: IP54
Photocell Wavelength: 940nm
Receiver Range: More Than 12m
Weight: 139g
A gate opener safety sensor is a crucial component of automated gate systems designed to prevent accidents and damage by detecting obstructions in the gate's path.
These sensors, often photoelectric, use an infrared beam to monitor the area and trigger the gate to stop or reverse if something is blocking its movement.
How it works:
-
Transmitter and Receiver:A safety sensor typically consists of a transmitter that emits an infrared light beam and a receiver that detects the beam.
-
Obstruction Detection:When an object, person, or vehicle interrupts the beam, the receiver signals the gate operator to stop or reverse the gate's movement.
-
Safety Feature:This mechanism prevents the gate from closing on anything or anyone, ensuring safety and preventing potential damage.
Types of Safety Sensors:
-
Photoelectric Sensors (Photo Eyes):These are the most common type, using an infrared beam to detect obstructions.
-
Safety Edges:These sensors are typically placed along the edge of the gate and trigger a stop or reverse when they encounter pressure.
-
Induction Loops:These sensors are embedded in the ground and detect vehicles as they pass over them, triggering the gate to open or close.
Importance:
-
Safety:The primary function is to prevent accidents and injuries by stopping or reversing the gate when an obstruction is present.
-
Preventing Damage:By detecting obstructions, these sensors help avoid damage to the gate, vehicles, or anything else in its path.
-
Compliance:Safety sensors are often required for automated gates to meet safety regulations and standards.
Common Issues:
-
Misalignment:If the sensor is misaligned, the infrared beam may not reach the receiver, causing the gate to malfunction.
-
Obstructions:Debris, dirt, or other obstructions can interfere with the beam and trigger false alarms.
-
Sensor Failure:Like any electronic device, sensors can fail over time, requiring replacement.
Safety sensor VEDO180
Ship or pick up from our office.
Safety sensor VEDO180
*NO/NC *AC/DC 12-24 V *Receiving Range: 25 Meters *IP 44Single Swing Driveway Gate, Picket Design, 12 ft
Ship or Pick up from our showroom at #100, 11538 132A Street, Surrey, BC.
Single Swing Driveway Gate, Picket Design, 12 ft
- Aluminum Picket design single swing driveway gate
- Gate Package Includes: 1 x driveway gate panel, 2 x steel gate posts (8' H by 4" x 4" each), 2 x Heavy duty adjustable steel hinges
- Material: Aluminum Tube Framing, Aluminum pickets with a black powder paint coating
- Gate Dimensions: 12' W x 6' H.
- No hidden fees
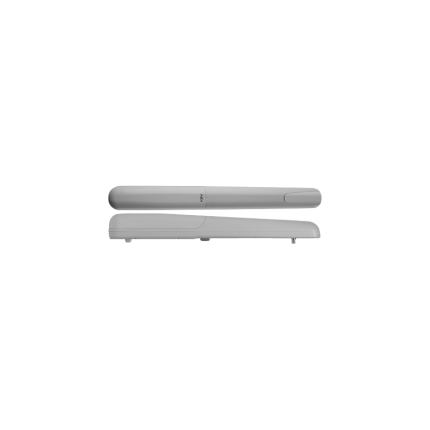
Single swing gate opener – VDS EGO24
Ship or pick up from our office.
Single swing gate opener - VDS EGO24
*Suitable gate weight: Maximum 200 Kg Included:- 1 x Electromechanical arm
- 1 x Main control board
- 1 x Waterproof box
- 2 x Remote control
- 1 x Safety sensor
- 1 x Manual release key