Ship or pick up from our office.
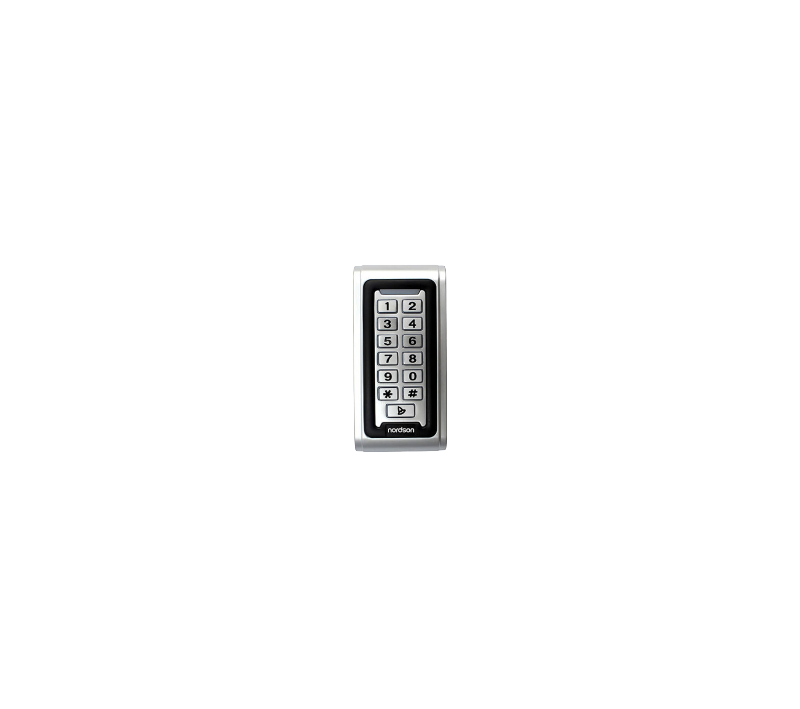
RFID Card Access Control
RFID card access control is a system that uses Radio Frequency Identification (RFID) technology to manage and control access to physical spaces. It provides a secure and convenient way to grant or deny entry to authorized individuals, replacing traditional keys or swipe cards.
This system works by wirelessly communicating between an RFID card (or tag) and an RFID reader.
How it Works
- RFID Card (Tag): Each authorized individual carries an RFID card, key fob, or even a smartphone with an embedded RFID chip. This chip contains a unique identification code and sometimes other encrypted data.
- RFID Reader: Readers are installed at entry points (doors, gates, elevators, etc.). They constantly emit a radio frequency field.
- Communication: When an RFID card enters the reader's field, the card's antenna captures energy from the reader's signal. This energizes the microchip on the card, allowing it to transmit its unique data back to the reader.
- Data Verification: The RFID reader decodes the information from the card and sends it to a central access control server or control panel. This server compares the card's data with a secure database of authorized users and their access permissions.
- Access Grant/Denial: If the credentials match an authorized profile, the system sends a signal to an electronic lock mechanism, allowing entry. If not, access is denied. This entire process typically happens in milliseconds.
- Audit Trail: The system also records detailed access information, including the time, date, and specific access point used, providing a valuable audit trail for security purposes.
Key Components
- RFID Cards/Tags: These are the credentials held by users, typically in the form of plastic cards, key fobs, or even integrated into mobile devices. They contain a microchip and an antenna.
- RFID Readers (Interrogators): Devices installed at entry points that emit radio waves to communicate with the tags and read their data.
- Access Control Panel/Server: This is the "brain" of the system. It receives data from the readers, verifies user credentials against a database, and controls the electronic locks. It can be cloud-based or local.
- Electronic Locks: Devices that secure the entry points and are controlled by the access control system (e.g., magnetic locks, electric strikes).
- Access Control Software: Software used to manage user profiles, set access levels, monitor events, and generate reports.
Types of RFID Tags
- Passive RFID Tags: Most common for access control. They don't have an internal battery and are powered by the electromagnetic field emitted by the reader. They have a shorter read range (a few centimeters to a meter).
- Active RFID Tags: These tags have their own power source (battery), allowing for a much longer read range (up to several hundred meters) and the ability to broadcast signals periodically. They are typically more expensive.
- Semi-Passive RFID Tags: These tags have a battery to power the chip but only transmit data when activated by a reader's signal, offering improved sensitivity and performance over passive tags.
Benefits of RFID Access Control
- Convenience: Offers contactless and keyless entry, making it fast and easy for users to gain access. Cards can often be read from inside a wallet or bag.
- Enhanced Security: Provides unique identification and can utilize encrypted communication, making tags difficult to duplicate. Lost cards can be immediately deactivated, preventing unauthorized use.
- Efficiency: Streamlines entry and exit processes, reducing wait times, especially in high-traffic areas.
- Flexibility & Scalability: Easily allows for adjusting access permissions for different users, areas, or time frames. Systems can be expanded or modified as needs change.
- Integration: Can be integrated with other security systems like CCTV, alarms, and time attendance systems for comprehensive security management.
- Audit Trails: Provides real-time tracking of who enters and exits, offering valuable data for security monitoring and incident investigation.
- Durability: RFID components generally experience less wear and tear compared to traditional mechanical locks or swipe card systems.
Security Considerations
While RFID access control offers many benefits, it's important to be aware of potential vulnerabilities:
- Skimming: In theory, unauthorized readers could attempt to read card information if they get close enough, though modern RFID cards often use one-time codes and encryption to mitigate this risk.
- Cloning: If the security protocols are weak, an RFID card's information could potentially be cloned.
- Electromagnetic Interference: Other electronic devices or metal/liquid objects can sometimes interfere with RFID signals, impacting performance.
To address these concerns, many RFID systems incorporate advanced encryption, mutual authentication, and integrate with multi-factor authentication methods. RFID-blocking wallets or sleeves are also available, though their necessity for security against typical skimming attempts is debated due to the short read range and other built-in card protections.
























Reviews
There are no reviews yet.